What Can Hackers Do with Your Phone Number? Risks and Prevention
Without a doubt, data theft currently represents one of the biggest risks online. If your phone number, email address, or other information falls into the wrong hands, it can be misused.
There are dozens of cases where a data breach results in spam calls, fraud, and even phishing. That's why it's so important to be well informed.
How Can Hackers Get Your Number?
Unfortunately, finding someone's phone number is very easy. In addition to data breaches, which is one of the most common ways criminals get your phone number, there are many other ways, including:
- Social media profiles: They often search social media platforms where some users who are not aware of privacy protection usually share their phone numbers.
- Data broker lists: A data broker collects and sells information about consumers, such as cell phone numbers and email addresses.
- The dark web: Criminals often buy and trade personal information on the dark web.
- Phishing scams: Cybercriminals collect information by sending deceptive messages via SMS, email, and other messaging apps.
- Dumpster diving: They may search through trash or packages to find confidential information, such as phone numbers. Be sure to destroy documents that contain your phone number and other personal information.
What Can Someone Do with Your Phone Number?
The first thing you're probably wondering is what people can do with your phone number. Well, you'd be surprised to learn what they can do with this simple piece of information. Here's the lowdown.
1Obtain Your Personal Info through Your Number
Hackers can find the information behind your phone number on social media or by using online reverse lookup services.
Once hackers have access to your number, they can use it to access your most sensitive and valuable data, for example:
- Social media data (your profile, information about your social friends, photos of you and your contacts, and your social experience, including your school and work history).
- Your name, location, and more via reverse lookup.
- Your date of birth and Social Security number (SSN).
- Financial assets and bank accounts.
2Spam and Harassment

One of the most common uses of phone numbers is harassment with spam or sales calls. One common practice is selling databases to call centers and telemarketing centers that buy filtered phones to harass customers with spam and telemarketing calls, from banks, and others.
3Use It for Phishing Scams
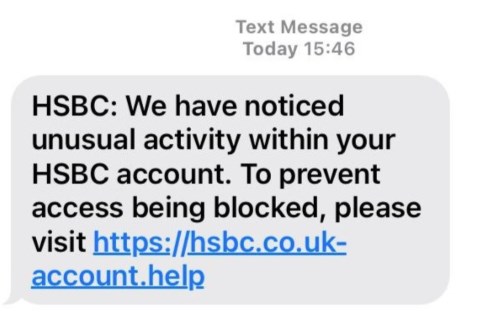
If your phone number was leaked, then it becomes a great opportunity for hackers to commit crimes. After getting your number, hackers will call you and trick you into thinking they're from a bank, a lottery company, etc.
Their goal is to make you fall into their trap and end up giving away valuable information or data that they can use, for example, to scam you, steal from you, take over your accounts, etc.
For example, it will send you a fake message or link via WhatsApp or SMS, telling you that you won the lottery or that your package delivery was abnormal.
4SIM Swap
If you don't know what SIM swapping is, you should know that it's a method in which criminals switch your phone to one of their own SIM cards. This way, they can steal your identity and take control of the accounts linked to your number.
- Hackers contact your phone provider by pretending to be you. They use the stolen personal information to bypass security controls.
- They ask the company to forward your calls and texts to their number. Once the forwarding is complete, they can intercept all your calls and texts.
- They can even access your account by selecting “Forgot Password” and then using the password reset link sent to your phone number to log in to your account.
- You can't make calls or send text messages.
- Get notifications about unfamiliar accounts’ activity.
- You cannot access the accounts.
- There are unauthorized transactions.
5Deceives Your Family and Friends
Sometimes, you may not be the victim, but your loved ones. In these scams, hackers use your number and information to pretend to be you and then trick your loved ones into sending money.
How to Protect Yourself Against Hackers?
To prevent hackers from taking over your phone number, you can follow these steps:
1Protect Your SIM with a PIN
A PIN is a type of password that prevents your SIM from being easily used. To create one, follow these steps:
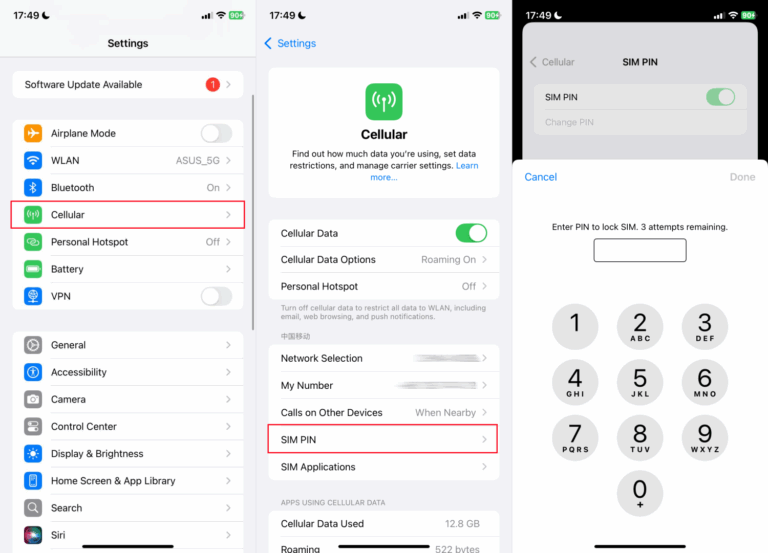
On iPhone
- Step 1. Go to “Settings.”
- Step 2. Click “Cellular.”
- Step 3. Then go to “SIM PIN” and activate the SIM PIN.
- Step 4. If prompted, enter your SIM PIN.
On Android
- Step 1. Go to “Settings” and tap Security & Privacy.
- Step 2. Select the SIM Lock option.
- Step 3. Activate the SIM lock option and enter the PIN code.
2Ignore and Block Spam Calls
A caller ID app can be a great way to identify potentially hacker or spam numbers. You can also use your phone's built-in features to block spam calls or messages. Here’s how:
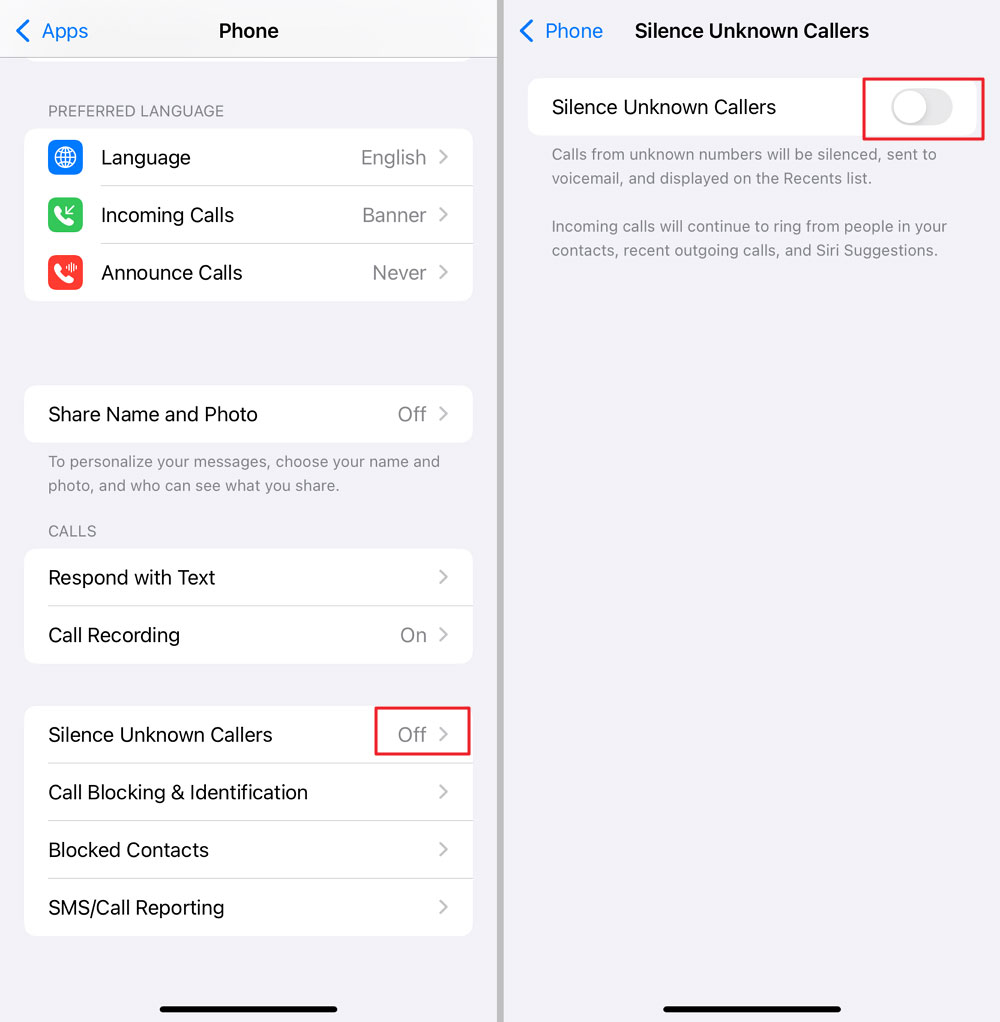
Silence unknown callers on iPhone
To turn this on, go to “Settings > Apps > Phone.” Then, scroll to the bottom, and select “Silence Unknown Callers.”
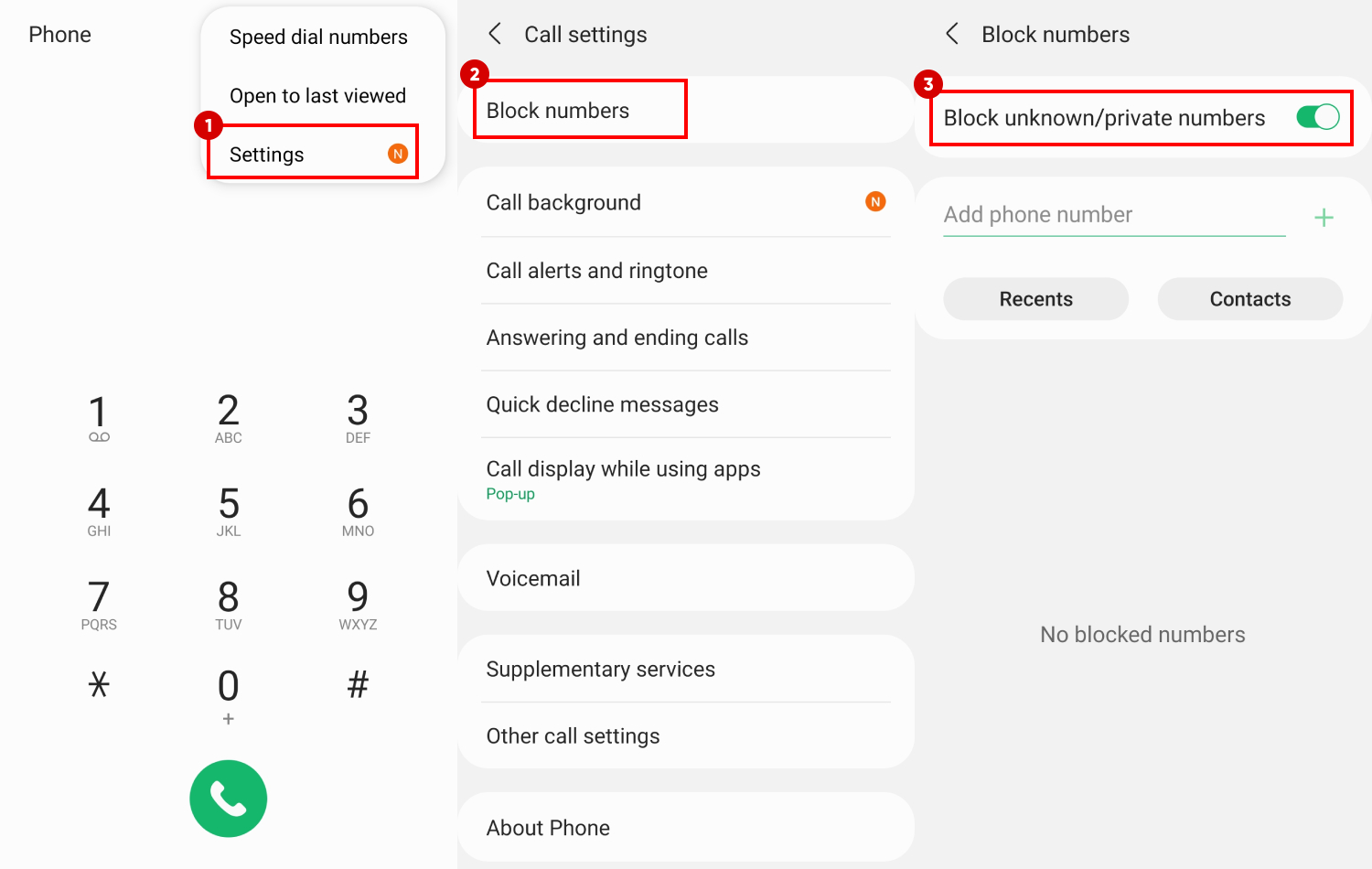
Filter spam calls on Android
Open the Phone app. Go to “Settings > Blocked Numbers. Then, turn on the "Block unknown/private numbers" switch.

3Enable MFA or 2FA authentication
If you don't want anyone to access your accounts, even if they have your phone number, email address, and password, you can enable two-factor or multi-factor authentication, which is an additional login filter. In addition to SMS, it's best to use it in conjunction with other types of MFA authentication, such as authenticator apps or biometric authentication.
4Install Antivirus App
One of the vehicles hackers use to break into phones is malware or viruses. These can come in files or apps of dubious origin, which is why it's so important to protect yourself.
Antivirus software designed for mobile devices is a good way to protect against this type of malware.
5Be Careful with Public Networks
Public or passwordless Wi-Fi networks are another avenue for compromised devices. Airports, parks, shopping malls, cafes, and more are all places where hackers can put your devices at risk.
It is recommended, for example, not to use sensitive apps like your banking apps on these types of networks, and if you do decide to use them, to protect yourself with a VPN.
6Turn off Bluetooth
Although not as common, a few years ago, Bluetooth connectivity was one of the most common methods for hacking devices. Many people make the mistake, for example, of leaving their Bluetooth enabled.
Among the Bluetooth hacking methods is the sending of documents, files, photos, etc. These can include, for example, malware.
7Do Not Click on Unknown Links
Finally, phishing is a common form of computer and account compromise. It basically involves sending a fake link to trick you into handing over emails, passwords, phone numbers, and more.
In the case of unknown files, it's basically sending compromised or malware-corrupted documents to hack your accounts.
How to Know If Your Phone Has Been Hacked
It's important to pay attention to the signs that your phone is hacked so you can take action. Pay close attention to these signs:
⚠️Performance issues: Usually, when a phone slows down, it's because there's a program running in the background without your knowledge, which could be a virus.
⚠️Overheated phone: The same thing happens with the temperature of the cell phone; when a program runs in the background, it overheats the phone.
⚠️Mysterious apps or data: When you notice a suspicious app or file you don't recognize, be very careful!
⚠️Fast battery drain: Programs running in the background can consume a lot of battery without you realizing it, draining it quickly.
⚠️Strange account’s activity: For example, password reset prompts or reset emails may be signs that someone is trying to hack you.
Conclusion
As you can see, hackers are increasingly at the forefront of improving their ability to steal your information and use it illegally. That's why it's so important to protect yourself.











Leave a Reply.