Device Monitoring Software: The Ultimate Guide for Security & Management [2025]
A restaurant chain owner noticed his phone frequently lagging and worried about customer order data being eavesdropped on. A healthcare IT manager needed to monitor the real-time status of 500 medical tablets while ensuring mobile device compliance and preventing sudden crashes while viewing medical records—both searched for "Device Monitoring Software," but their needs were drastically different: the former wanted to "prevent malicious monitoring," while the latter required "Enterprise Mobile Device Management (MDM) and compliance."
The concept of "device monitoring" is often confused in the market. Some equate it with "spyware," while others use it to ensure business continuity. This article will help you clarify the boundaries:
First, it teaches you how to identify and remove unauthorized monitoring; then, it details how enterprises can achieve a dual improvement in "security + efficiency" through legitimate tools; and finally, it helps you find a solution suitable for your specific scenario.
Understanding Device Monitoring: From Security Threats to Business Tools
What is Covert Monitoring Software? (The Spyware Threat)
Covert monitoring software is malicious software that secretly collects device data without authorization. It is typically implanted in three ways: disguised as legitimate apps like "system update" or "office software" to lure users into downloading; forcibly installed via phishing links or USB devices; and silently infiltrating the device's system by exploiting vulnerabilities.
Its core harms lie in two areas:
Privacy theft
Recording phone calls, text messages, location information, or chat logs and document editing content on computers. There have been cases where companies suffered serious financial losses due to the leakage of core trade secrets after such software was implanted on employee computers.
System damage
Continuously consuming CPU and memory in the background, causing device lag, rapid battery drain, and even tampering with system settings to prevent users from installing security patches.
Key distinction
The essence of this type of software is "secret monitoring without consent," which is fundamentally different from "legal corporate monitoring" discussed later—the latter requires prior notification to employees/device users, and the monitoring scope is strictly limited to "corporate IT asset operation data," not involving personal privacy.
Legitimate Business Device Monitoring Software
The core positioning of enterprise-level equipment monitoring software is a "Remote Monitoring and Management (RMM) tool", not a "privacy spying tool". It must meet two prerequisites: a "Monitoring Notification Agreement" must be signed with the user in advance, clearly defining the scope of monitoring; and the data must be used solely for "equipment maintenance, security compliance, and business assurance," and not for tracing personal behavior.

Based on enterprise scenarios, it is mainly divided into three categories to precisely match different monitoring needs:
Endpoint device monitoring
Targeting terminal devices such as employee computers, Android POS machines, and medical tablets, focusing on "hardware health" and "software compliance." For example, retail stores use it to view the CPU usage of POS machines in real time, and automatically issue alerts when the value exceeds 95% to prevent sudden lag during checkout; medical institutions monitor whether medical tablets are "copying medical records to personal USB drives" to comply with HIPAA and other compliance requirements.
Network device monitoring
This focuses on network infrastructure such as routers, switches, and servers, with an emphasis on "abnormal traffic" and "bandwidth allocation." For example, the IT team uses tools to detect a sudden surge in upload traffic on a department's server and promptly intercepts it to prevent network congestion.
IoT Device Monitoring
For IoT devices such as logistics vehicle terminals and factory sensors, the focus is on "offline status" and "data transmission integrity." For example, logistics companies use it to monitor Android terminals on trucks. If the device is offline for more than 1 hour, an alarm is automatically pushed to the operations and maintenance team to prevent the loss of transportation data.
Enhance Your Enterprise Device Management with AirDroid Business
Discover how AirDroid Business provides a comprehensive Remote Monitoring and Management (RMM) solution, ensuring device security and operational efficiency. With features like real-time monitoring, remote control, and compliance management, it's designed to meet the diverse needs of modern enterprises.
How to Detect Unauthorized Monitoring on Your Personal Devices

The question is, how can you tell if your personal devices, like your phone or your computer, have monitoring software installed to spy upon your data without you knowing. Here are the common signs to look for.
Signs Your Phone May Have Monitoring Software
After a mobile phone is infected with hidden monitoring software, a series of verifiable abnormal signals will appear, which can be identified without professional technical expertise:
Hardware level
Battery drains significantly faster when not in use (background programs continuously collect and upload data); the phone frequently overheats, even after closing all apps (malicious processes consume large amounts of CPU resources).
Network level
The mobile data bill shows "abnormal consumption during off-network periods", such as tens of MB of mobile data usage even after Wi-Fi is turned off at night; Wi-Fi or Bluetooth automatically connects to unfamiliar devices, and connection records cannot be manually deleted.
Operation level
Screen response is delayed, such as an app taking 2-3 seconds to open after clicking; a vaguely named notification appears in the notification bar (e.g., "System services have been updated"), and clicking it does not redirect to a new page; unfamiliar numbers suddenly appear in the contacts or call log, and cannot be deleted.
Immediate troubleshooting steps
Go to your phone's "Settings - Application Management" and check for suspicious apps with "no icon or vague name", such as "winmonitor" or "phonetrack". These types of software often disguise themselves as "system tools". If you find them, uninstall them immediately and restart your phone.
How to check if Your Computer is Being Monitored
Hidden monitoring software on computers is harder to detect, but it can be accurately identified through three steps applicable to both Windows and macOS systems:
Check background processes
Windows users press "Ctrl+Shift+Esc" to open "Task Manager," while macOS users access it through "Launchpad - Other - Activity Monitor." Filter for processes with "CPU usage exceeding 50%" and "ambiguous developer names." For example, processes named "monitor.exe" or "macspy," if their purpose cannot be identified, are likely malicious programs. Right-click and select "End Process."
Check network connectivity
Windows users can type **"netstat -ano"** in the "Command Prompt" to check for persistent connections from unfamiliar IP addresses (the location can be verified using an "IP address lookup tool"; if the IP is located overseas or has no clear organization, it should be disconnected immediately); macOS users can check whether the "Router" and "DNS Server" are set to default addresses through "System Settings - Network - Advanced - TCP/IP". If they have been changed to unfamiliar addresses, it may be due to tampering by monitoring software.
Check for hidden software
On Windows, go to "Control Panel - Programs and Features"; on macOS, go to the "Applications" folder. Uninstall any unknown software whose names contain "monitoring," "tracking," or "logging." Also, delete any suspicious plugins in your browser extensions (such as "webpage screenshot tool" or "history backup," which may contain hidden monitoring functions).
Tools and Apps to Find Network Anomalies
To address the questions of "how to discover hidden surveillance devices" and "troubleshooting abnormal network connections," we recommend three types of practical tools, covering different needs for home, small business, and enterprise users:
For home/small business users
Prioritize lightweight tools that are easy to use and free. For example, Fing (the mobile app) can scan all online devices after connecting to Wi-Fi and label the device type (e.g., "smartphone," "camera," "computer"). If it finds an unidentified "unknown device" (e.g., "Generic Camera"), it may be an illegal surveillance camera; or use the system's built-in traffic monitor to check data consumption during off-network periods.
For enterprise users
It's recommended to use professional tools to balance monitoring and security. For example, Nessus (a network vulnerability scanner) can detect the risk of "surveillance backdoors being implanted" in the enterprise network.
AirDroid Business (an Android device management tool) can not only monitor the network connection status of enterprise Android devices, but also identify "employees connecting to unauthorized hotspots," preventing devices from being compromised by illegal monitoring software.
Real-world example
An employee of a company noticed that their computer's internet speed was slow. Using Fing to scan the office Wi-Fi, they discovered an "unknown device" continuously connecting, with the device type labeled "Unknown." After on-site investigation by the operations team, an illegally installed surveillance camera was found in a corner of the meeting room and was promptly removed to prevent data leakage.
Protect Your Devices with AirDroid Business
Safeguard your organization's devices against unauthorized monitoring and potential security threats. AirDroid Business offers advanced monitoring capabilities, allowing you to detect anomalies and ensure compliance across all devices.
The Business Case for Legitimate Device Monitoring Solutions
Key Features of Enterprise Device Monitoring Software
High-quality enterprise-grade monitoring software goes beyond simply "viewing data"; it addresses "problems." Its core functionalities should cover the following three points:
1. Multi-dimensional Monitoring:
Comprehensive Understanding of Device Status. This includes monitoring not only basic hardware metrics such as CPU, memory, and disk, but also tracking software compliance. For example, it should support "unauthorized app blocking," automatically blocking and sending alerts to administrators when employees install games on POS machines; and recording "peripheral connection logs," detailing when a device connected a USB drive and copied files, facilitating subsequent compliance audits.
For weak network scenarios, it should also support "offline data caching"—when logistics vehicle terminals are in remote areas without signal, monitoring data can be stored and automatically synchronized to the backend upon network connection, preventing data loss.
2. Intelligent Alerts:
Avoiding Alert Bombardment and Missed Alerts. Supports customizable alert rules based on "severity," rather than pushing notifications for every anomaly. For example, setting alerts like "CPU usage exceeding 90% (urgent, SMS + WeChat Work dual alert)" or "Disk space less than 20% (important, WeChat Work alert)" helps the IT team focus on core issues.
After implementing this feature, a chain retail company saw a significant improvement in the alert handling efficiency of its operations team, no longer being distracted by low-priority information.
3. Remote Intervention:
From "Discovering Problems" to "Solving Problems" Basic monitoring tools can only "detect anomalies," while enterprise-level tools need to support "remote operation." For example, if the IT team discovers a POS machine in a store has a "barcode scanner connection failure" through AirDroid Business, they can restore the connection by remotely restarting the device's USB interface service without sending anyone to the site for investigation; if an employee reports a computer lag, the administrator can remotely close high-utilization background processes to quickly resolve the issue.
Remote Monitoring Software for Employees: Boosting Productivity and Security

In remote work scenarios, the core value of device monitoring software is "ensuring business efficiency", rather than "monitoring employee behavior." Three principles must be adhered to: do not monitor personal privacy content, clearly define the monitoring scope in advance, and use data only for device maintenance.
Specific application scenarios include:
1. Productivity Assurance:
Monitor "application usage time," but only calculate the ratio of "office software" to "non-work software," without recording specific operations. One internet company, after using this function, effectively improved the efficiency of remote employees by "optimizing device lag issues" (such as remotely clearing memory).
2. Security Protection:
Provide real-time alerts for "device security risks," such as employee computers connecting to unfamiliar Wi-Fi networks or installing pirated office software. A foreign trade company used this function to effectively prevent "employee’s mistakenly copying customer contracts to personal USB drives," avoiding the leakage of trade secrets.
3. Compliance Management:
For industries such as finance and healthcare, monitor whether "devices meet security standards." For example, if a bank requires employees' computers to have firewalls enabled and specific antivirus software installed, the tool can automatically detect and push a "list of non-compliant devices," allowing administrators to remotely assist in configuration and avoid compliance penalties.
Beyond Employees: Network Device Monitoring
The core difference between network device monitoring and "employee endpoint monitoring" lies in their focus: the former prioritizes "infrastructure stability," while the latter focuses on "endpoint device availability." Both must be used in conjunction to cover the entire enterprise ecosystem.
Common network device monitoring tools (such as Datadog and SolarWinds) primarily address three types of issues:
1. Network topology visualization:
Displaying the connection relationships of routers, switches, and servers, intuitively showing "which devices are affected by a network outage in a certain department."
2. Traffic anomaly tracing:
Monitoring "incoming and outgoing network data packets" to identify issues such as "virus attacks" and "large file bandwidth abuse."
3. Bandwidth allocation optimization:
Allocating bandwidth according to "department/business priority" to ensure core business operations are unaffected.
It's important to note that these tools are more suitable for "IT operations teams managing network infrastructure." If the core need of an enterprise is "monitoring Android POS machines, tablets, and other terminal devices", then a "dedicated endpoint device monitoring tool" like AirDroid Business should be chosen—it not only monitors device status but also allows remote control and patch pushes, forming a closed loop of "monitoring-management-repair."
Streamline Your Device Management with AirDroid Business
Elevate your business operations with AirDroid Business's all-in-one device management platform. From proactive monitoring to remote troubleshooting, our solution empowers your IT team to maintain optimal device performance and security.
Choosing the Right Device Monitoring Software for Your Needs
Here’s a complete guide to getting your hands on the most suitable device monitoring software that suits your needs.
Free vs. Paid Solutions: What to Consider
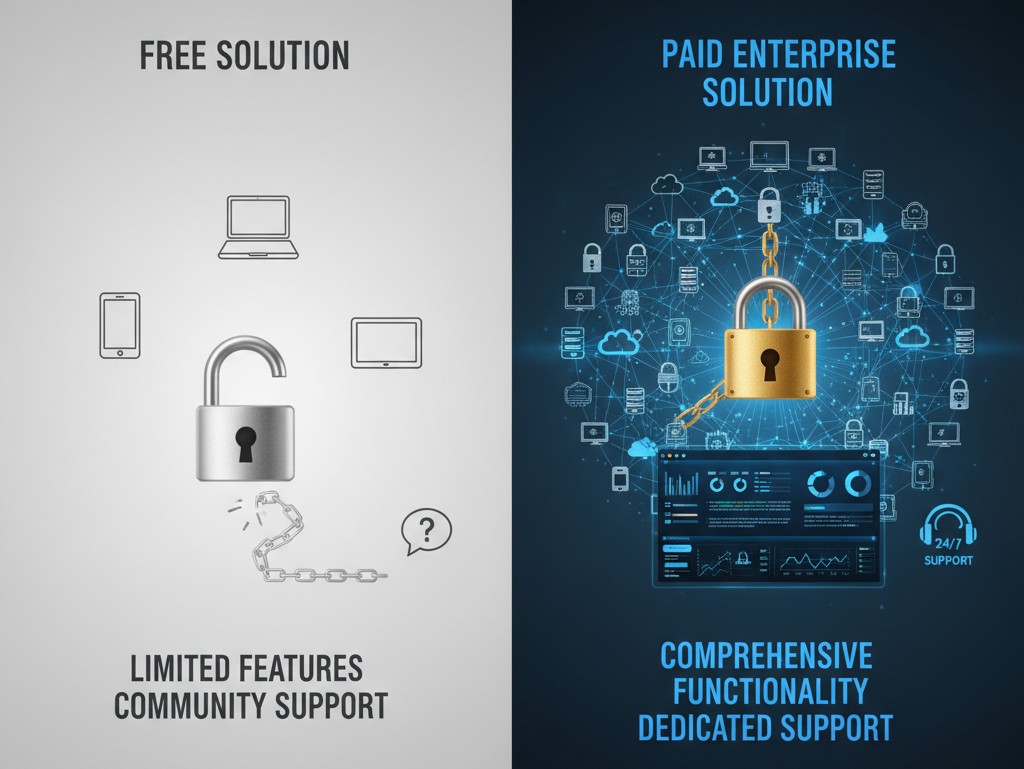
The difference between free tools and paid enterprise versions lies not only in the number of features, but also in security, scalability, and technical support. The choice should be made based on the size and needs of the enterprise.
| Comparison Dimension | Free Solutions (e.g., Fing Basic, Nagios Core) | Paid Enterprise Editions (e.g., AirDroid Business, ManageEngine) |
|---|---|---|
| Device Support Quantity | Limited to 10–20 devices; additional devices must be added manually | Easy to scale; supports Excel batch import; suitable for managing 100+ devices |
| Core Features | Basic monitoring only (e.g., online status, CPU usage); no alerts or remote control | Comprehensive functionality: intelligent alerts, remote intervention, compliance logging, offline data caching |
| Data Security | Data stored on third-party cloud servers; no localization options, higher compliance risk | Supports on-premises or private cloud deployment; data transmission secured with TLS 1.3 + AES-256 encryption |
| Technical Support | Community forum only; response time 1–3 days | 24/7 human support; issue response within 1 hour; on-site training available |
Decision Recommendations:
For small businesses or households with fewer than 5 employees, the free tool can meet basic monitoring needs (such as viewing Wi-Fi connected devices); for businesses with more than 10 employees, geographically dispersed devices, or high compliance requirements (such as retail and healthcare), it is recommended to choose the paid version.
A chain restaurant once used the free tool to monitor 50 POS machines, but data was lost due to the lack of offline caching. After switching to a professional paid tool, data integrity was greatly improved and maintenance costs were effectively reduced.
AirDroid Business: Beyond Basic Monitoring to Comprehensive MDM

AirDroid Business differs from "tools that only monitor" in that it is an "integrated monitoring and management platform specifically for Android endpoint devices", especially suitable for enterprises with a high proportion of Android devices (such as retail, healthcare, and logistics). Its core advantages are concentrated in three points:
1. Focusing on Android Scenarios to Solve Industry Pain Points
- Retail Scenarios:
Monitors the "hardware health" and "software running status" of POS machines. When the POS machine's "memory usage exceeds 95%", it automatically pushes an alarm and clears background processes; supports "batch push of system patches" to avoid omissions caused by manual operation. - Medical Scenarios:
Monitors the "network connection (only allowing connection to hospital Wi-Fi)" and "operation log (whether medical records are copied)" of medical tablets. Logs are automatically retained, complying with HIPAA regulations; if the tablet is lost, device data can be remotely erased to prevent patient privacy leaks. - Logistics Scenarios:
Monitors the "offline status" and "GPS positioning" of in-vehicle Android terminals. Automatically caches transportation data in weak network environments and synchronizes it after connecting to the network; supports "remote updates of navigation maps".
2. Closed-Loop Capability from "Monitoring" to "Management"
It goes beyond simply "viewing data," enabling proactive problem-solving:
- Centralized Monitoring:
View the status of devices nationwide on a single dashboard, eliminating the need to switch between multiple platforms. - Remote Control:
Administrators can remotely connect to devices, shut down abnormal processes, clear caches, and quickly restore functionality. - Compliance Management:
Supports "device group authorization," allowing store managers to view only devices within their own store, while headquarters IT can manage all devices, preventing data leaks; automatically generates "device monitoring logs" for easy export during audits.
3. Balance between security and ease of use:
No professional IT team required to get started: Provides "template-based configuration", such as the retail industry can directly import "POS machine monitoring templates" without manually setting alarm thresholds; supports "mobile APP management", so that administrators can check device status and receive emergency alarms even when they are away.
Conclusion: Empowering Your Business with Transparent Device Monitoring
Legitimate device monitoring software is not a "tool for companies to monitor employees," but rather a "powerful tool for ensuring business continuity, reducing operational costs, and meeting compliance requirements." When choosing such software, three core principles should be considered: clearly define the monitoring scope to avoid infringing on personal privacy; match the software to your specific needs—choose dedicated tools like AirDroid Business if you have many Android devices, or platforms like Datadog if you have many network devices; and prioritize integrated "monitoring + management" tools to avoid ineffective monitoring that only involves "viewing without making changes."
If your business is struggling with issues like slow device troubleshooting, difficult Android terminal management, and time-consuming compliance audits, consider starting with a trial:
Main CTA:
Apply for a 14-day free trial of AirDroid Business (supports 100 devices) to experience real-time monitoring, remote control, and compliance management features for Android terminals, adaptable to various scenarios in retail, healthcare, and logistics.
Secondary CTA:
Download the free guide "Best Practices for Android Endpoint Device Monitoring" to learn how to design monitoring solutions for POS machines, tablets, and other devices to optimize operational efficiency.







Leave a Reply.