Android Enterprise Security Guide: MDM's 6 Strategies for Data Protection
A single, unmanaged Android device could be the one weak link in a catastrophic data breach. In an era where corporate data flows freely across countless mobile endpoints, is your business truly prepared to defend its most valuable assets?
The traditional security perimeter has dissolved. Mobile Device Management (MDM) for Android is no longer just a tool; it's a strategic shift. It transforms your security posture from reactive defense to proactive control, making it the cornerstone of any modern enterprise mobile strategy. This guide goes beyond a simple list. We'll dissect the security logic behind six core MDM strategies and provide the actionable steps you need to build a truly resilient mobile ecosystem.
1The Strategic Value of MDM Security
In the mobile era, legacy security models like device-level antivirus are insufficient. They can't address threats posed by insecure networks, risky user behavior, or non-compliant applications. Modern security demands a more intelligent approach built on principles like "Zero Trust" and "least privilege." This is where the value of an MDM solution truly shines.
This is where an MDM solution shines. It doesn't just build a wall; it creates a dynamic, intelligent security framework. It assesses every device, user, and access request to build a comprehensive defense system that protects data from the endpoint to the cloud, empowering your workforce to be productive without compromising security.
26 Core MDM Security Strategies in Practice
Here are the six essential strategies that form the foundation of a robust Android security program, all achievable through a powerful MDM platform.
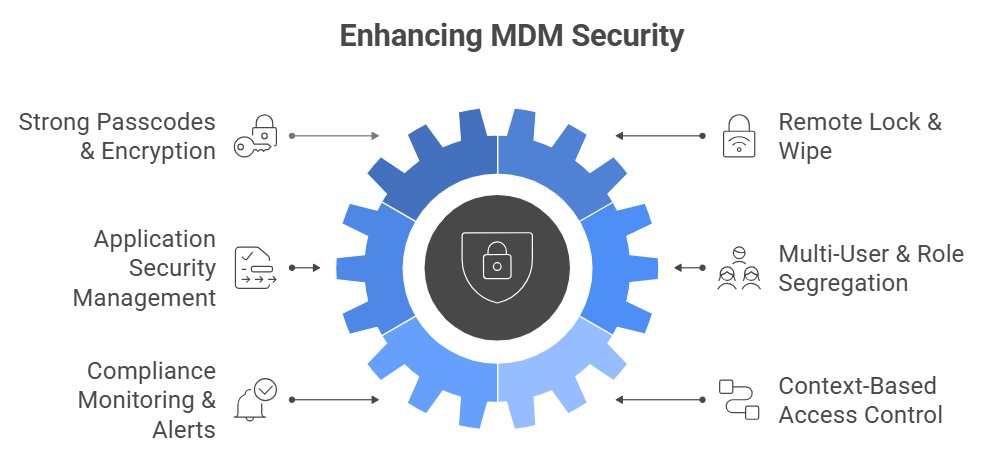
Strategy 1: Enforce Strong Passcodes & Data Encryption
The Logic: Full-disk encryption is your last line of defense. It ensures all data stored on a device is cryptographically scrambled. Even if a device is physically stolen, the data remains unreadable without the decryption key—the user's passcode. A weak passcode renders strong encryption useless.
Actionable Steps: Use your MDM to enforce strict passcode policies. Mandate minimum length, complexity (requiring letters, numbers, and symbols), and set automatic expiration periods. This simple, automated step dramatically elevates the security baseline for every device.
Strategy 2: Master Remote Lock & Wipe Capabilities
The Logic: When a device is lost or stolen, time is critical. MDM allows IT admins to instantly and remotely lock a device to prevent access or wipe its data to prevent a breach. Crucially, this can be automated. MDM can execute these commands based on triggers—like a device being offline for too long or multiple failed login attempts—slashing response time from hours to minutes.
Actionable Steps: Configure automated security rules. When handling BYOD and data security, it's crucial to find the right balance between device management and employee privacy. Differentiate between a selective wipe (removing only corporate data and apps, ideal for BYOD) and a full wipe (factory resetting the device).
Strategy 3: Implement Application Security Management (Allow/Blocklists)
The Logic: Malicious applications are a primary vector for malware and data theft. An MDM's application management feature cuts off this threat at the source. By creating "allowlists" (whitelists) of approved apps and "blocklists" (blacklists) of forbidden ones, you control the entire software ecosystem on corporate devices. Distributing apps through a managed enterprise app store further ensures version control and security,especially for devices secured in a lockdown mode.
Actionable Steps: Establish and maintain application allowlists for all managed devices. Use the MDM console to push mandatory apps, install updates, and uninstall non-compliant software remotely.
Strategy 4: Utilize Multi-User & Role Segregation
The Logic: Adhering to the "principle of least privilege" is fundamental to minimizing internal data exposure. Not every employee needs access to every corporate app or dataset. MDM allows you to create distinct profiles for different roles or teams, ensuring users can only access the specific resources required for their job.
Actionable Steps: Create unique device profiles for your sales, logistics, and management teams. For example, the logistics team's devices might be locked into a single delivery app, while the sales team has access to CRM and email clients.
Strategy 5: Establish Compliance Monitoring & Automated Alerts
The Logic: An MDM acts as your 24/7 digital sentry, continuously monitoring the health and status of every device. It instantly detects non-compliant activities that could signal a threat, such as a device being jailbroken (rooted), a security feature being disabled, or the installation of a blacklisted app.
Actionable Steps: Configure automated alerts for compliance violations. Set up rules that trigger immediate action, such as automatically disconnecting a non-compliant device from the corporate network or locking it until an admin can review the issue.
Strategy 6: Adopt Context-Based Access Control (Zero Trust)
The Logic: The core idea of Zero Trust is "never trust, always verify." A sophisticated MDM applies this by dynamically assessing a device's right to access corporate resources based on its real-time context. It evaluates the device's security posture, network environment, location, and more before granting access.
Actionable Steps: Implement policies that restrict access to sensitive data based on context. For example, if an employee connects to an unsecured public Wi-Fi at an airport, the MDM can automatically block their access to the company's internal file server while still allowing access to less sensitive resources like email.
3Conclusion: Your Next Steps Toward Total Security
Implementing these six strategies transforms MDM from a simple management tool into a strategic asset for proactive security, enhanced efficiency, and business empowerment. Together, they create a modern, layered security architecture that protects your data wherever it goes.
Ready to put these principles into action?
AirDroid Business - Comprehensive MDM solution
AirDroid Business is the ideal platform to implement these strategies seamlessly. Start your free trial today and experience the leap in efficiency and security that MDM provides.







Leave a Reply.