What is Android Certificate Management?
1Is your enterprise facing these certificate management challenges?
In daily business operations, the security issues of Android devices are often hidden behind seemingly normal activities. Many enterprises have blind spots in certificate management and may face the following risks:
- 1. Sensitive data “exposed” on public Wi-Fi: When employees work remotely, customer order data on their phones may be leaked due to unencrypted connections.
- 2. Unverified “rogue apps”: Applications lacking signature verification may be maliciously tampered with, creating security risks for devices, making them un-installable, or causing business interruptions.
- 3. Sudden disruption of critical business: A frustrating scenario—one morning, team members suddenly find that Android devices cannot connect to the corporate VPN. After checking the logs, it turns out the certificate has expired, causing operations to come to a halt.

These problems are not hypothetical; they are real challenges enterprises often face when managing certificates manually. Many people might think certificate management is just a small matter for the IT department and that having a firewall and antivirus software is enough. In reality, Android certificate management is the foundation of an enterprise’s security system. Whether it’s a small team of dozens or a large group of thousands, as long as Android devices are in use, certificate management must be taken seriously.
2What is an Android Certificate? How Does It Work?
What is an Android Certificate? — The “Digital ID” for Devices and Applications

Simply put, an Android certificate is like an ID card in real life, an electronic file that proves the legitimacy of identity. For example, when an Android device wants to access a corporate intranet, it must present a “device identity certificate” to prove it is a company-approved device. When an app wants to be installed on enterprise devices, it needs a “code signing certificate” to show that it is an officially developed, risk-free application.
In addition, every Android certificate has its own unique digital number, secured through encryption technology to prevent forgery. Just like the security features on an ID card, this helps effectively eliminate cases of impersonation. Let’s take a closer look at the common types and uses of certificates in real scenarios.
Common Types and Uses of Certificates
Now that you know what an Android certificate is, let’s have a look at its various types and their role.
SSL/TLS Certificates — The “Security Lock” of Network Communication
Its core function is to “lock” the communication between devices and servers, preventing data from being stolen or tampered with during transmission. For example, when store employees of a retail chain use Android tablets to record daily sales data, the SSL certificate encrypts it so that as the data travels from the tablet to the headquarters server, hackers see only unreadable garbled text, not the actual information.
Without an SSL certificate, the data would be sent in plain text, exposing business secrets. This highlights the need for Device Identity Certificates to control which devices can access corporate resources.
Device Identity Certificates
It works like a “special access card” issued by the enterprise to Android devices. Only devices holding this access card can connect to the corporate VPN, access internal databases, and other core resources.
When a new employee joins, the IT department installs a device identity certificate on their Android work device, completing the “identity binding.” Upon leaving, the certificate is revoked, preventing the device from accessing the corporate network. For example, when a developer at an internet company resigns, their Android development tablet can no longer access the company’s code repository, effectively preventing core code leaks.
Code Signing Certificates — The “Safety Pass” for Apps
Enterprises often use self-developed apps or customized business apps (such as cargo tracking apps in logistics or patient information inquiry apps in healthcare), and the code signing certificate serves as the “safety pass” for these apps. When the enterprise deploys an app to employees’ Android devices, the system verifies the app’s identity through the certificate and only enterprise-signed apps can be installed. If it’s an unsigned pirated app or malware, the system blocks it directly, preventing devices from being compromised.
For example, a healthcare company equips nurses with Android terminals and, via code signing certificates, allows only the official patient care app, preventing accidental installation of software that could leak sensitive medical data.
To understand why certificates are so reliable, we need to look at their core components and the trust mechanism behind them.
Comprehensive Certificate Management with AirDroid Business
Managing various certificate types can be daunting. AirDroid Business simplifies this by providing a centralized platform to handle SSL/TLS, device identity, and code signing certificates, enhancing your organization's security posture.
3Core Components and Trust Mechanism of Certificates
So, how are these certificates trusted and managed? Their functioning relies on a complete Public Key Infrastructure (PKI), and the following are its key components:
CA (Certificate Authority): The “Issuing Authority” of the “Digital ID”
CA (Certificate Authority) is the authoritative organization responsible for issuing, managing, and verifying certificates. Its core responsibility is to ensure the “legitimacy” and “validity” of certificates—only certificates reviewed and issued by a CA can be trusted and recognized by Android devices.
In terms of types, CAs are mainly divided into two categories:
Public CA:
- This type of CA is a widely recognized authority, and the certificates it issues have strong compatibility, being recognized by almost all Android devices. It is suitable for enterprises’ formal business scenarios. For example, when an enterprise needs to deploy certificates for customer-facing kiosk devices, it must apply from a third-party CA to ensure the devices can be used normally.
Private CA:
- This type of CA is managed by the enterprise itself, without the need to apply to third-party organizations. It has low cost and fast generation speed, but lower security, and the certificates it generates may not be trusted by some Android devices. It is only suitable for internal enterprise testing scenarios (such as when the R&D team tests self-developed apps).
When choosing a CA, enterprises should consider their needs: if it is for formal business use, a public CA should be the priority to ensure certificate compatibility and security; for internal testing, a private CA can meet the needs, but it should not be used in a formal environment. Next, understanding Public and Private Keys is essential, as they are the core keys for encryption and decryption.
Public Key, Private Key: The “Keys” for Encryption and Decryption

The Core Principle of Asymmetric Encryption
The public key and private key are the “core tools” of the certificate encryption system. They are a pair of matching “keys” that must be used together to achieve data encryption and decryption.
Public Key:
- Public Key: Equivalent to a “public encryption key,” it can be freely distributed to the enterprise’s Android devices, partner servers, etc., and is used to encrypt data. For example, headquarters distributes the public key to all store Android devices, which use it to encrypt sales data before transmitting it back to headquarters.
Private Key:
- Private Key: Equivalent to a “confidential decryption key,” it is held only by the enterprise itself (usually the headquarters server) and must not be disclosed to anyone. It is used to decrypt the data encrypted by the public key. After the headquarters receives the encrypted data transmitted by the store devices, it uses the private key to decrypt it and obtain the real sales data.
The public and private keys are mathematically linked, but the private key cannot be derived from the public key. Anyone can encrypt data with the public key, but only the holder of the private key can decrypt it, ensuring confidentiality.
Even if the public key is obtained by hackers, without the corresponding private key, they cannot decrypt the data; conversely, if the private key is leaked, even if the public key is secure, the data will still face the risk of exposure. Therefore, enterprises must properly safeguard the private key, storing it on secure servers with strictly controlled access permissions, to prevent the private key from being lost or stolen.
This is where the Android KeyStore comes in, acting as a “safe box” for securely storing certificates.
Android KeyStore: The “Safe Box” for Securely Storing Certificates
In the Android ecosystem, certificates are not arbitrarily stored in device memory. To ensure their security, the Android system provides a dedicated hardware-level or software-level secure area called the Android KeyStore.
You can think of the Android KeyStore as a highly secure “safe box” on the device, where all important keys and certificates are stored.
Trust Levels: The “Security Guards” of Certificates
Inside this “safe box,” certificates are categorized and assigned different trust levels.
System-level trust: The Android system has built-in trust for certain authoritative certificate authorities (such as Google). These certificates are usually stored in the system-level KeyStore, considered the highest level of trust, and are used to verify important system updates or core services.
User-level trust: Some certificates are manually installed by users or IT administrators, such as internal enterprise CA certificates. These certificates have a lower trust level than system certificates, are usually accompanied by additional security prompts, and can be manually removed by users.
This layered approach ensures devices trust only authorized certificates while minimizing risks. Next, the storage location of certificates, combining hardware and software, further protects them.
Storage Location: Collaboration Between Hardware and Software
The storage location of certificates directly determines their security level.
Hardware-level storage: On supported devices, the Android system stores certificates and private keys in a Hardware Security Module (HSM). This physically isolated storage method can effectively resist theft by malicious software—even if the device is rooted, attackers cannot easily obtain this sensitive information.
Software-level storage: On devices without a hardware security module, certificates are stored inside the device in the form of encrypted files. Although not as secure as hardware storage, the Android system still provides strong encryption protection.
Proper storage and trust assignment set the foundation for the chain of trust, which ensures devices recognize and accept only legitimate certificates.
Chain of Trust: Making Devices “Believe” Certificates Are Legitimate
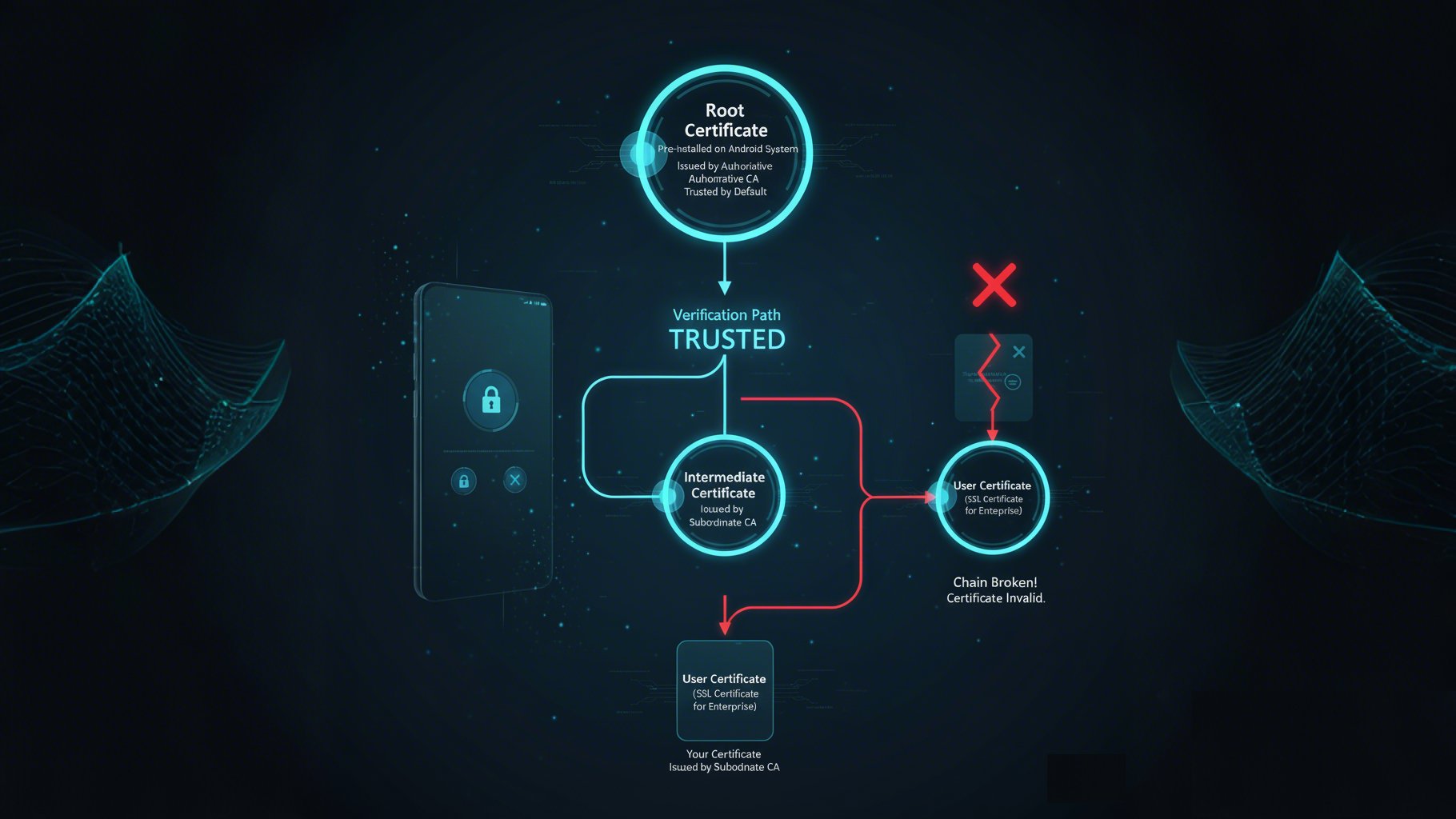
Many enterprises may encounter this problem: even though a certificate has been installed on an Android device, it still shows “certificate invalid” or “cannot be trusted,” causing the device to be unusable. The reason behind this is most likely a “broken chain of trust”—the device does not recognize the “legitimacy” of this certificate.
So, what is the chain of trust? Simply put, the chain of trust is a verification chain composed of “root certificate → intermediate certificate → user certificate,” used to prove the legitimacy of the user certificate (the certificate actually used by the enterprise). Among them:
Root Certificate:
It is the “starting point” of the chain of trust, issued by an authoritative CA and pre-installed in the Android device’s system. The device by default trusts all CA organizations corresponding to root certificates;
Intermediate Certificate:
It is the “bridge” connecting the root certificate and the user certificate, issued by a subordinate CA authorized by the root certificate’s CA;
User Certificate
It is the certificate actually used by the enterprise (such as device identity certificates or SSL certificates), issued by the subordinate CA corresponding to the intermediate certificate.
When an Android device receives a user certificate, it verifies it step by step along the chain “user certificate → intermediate certificate → root certificate”: if it can ultimately trace back to a root certificate trusted by the device, the user certificate is considered legitimate; if any link in the middle is missing (for example, the intermediate certificate is absent) or it cannot be traced back to the root certificate, the device will show “certificate invalid.”
For example, an enterprise obtains an SSL certificate from a third-party CA, issued via an intermediate certificate linked to a root certificate. When the enterprise installs the SSL certificate on an Android device, the device first verifies whether the SSL certificate was issued by the intermediate certificate, then verifies whether the intermediate certificate was issued by the root certificate—since the root certificate is pre-installed on the device, once verification passes, the device will trust the SSL certificate and allow encrypted data transmission.
If the enterprise forgets to install the corresponding intermediate certificate when installing the SSL certificate, the chain breaks and the device shows “certificate invalid,” leaving data unencrypted. Therefore, when deploying certificates, enterprises must install both the user and corresponding intermediate certificates to maintain the chain of trust and ensure proper device operation, which is why effective Android certificate management is vital.
4Why Android Certificate Management Is Crucial for Your Enterprise
So, why should enterprises value comprehensive Android certificate management and what will be the consequences of neglect? Below are the reasons why it matters.
Ensure Device Identity: Allow Only “Enterprise-Approved Devices” to Access Resources

Enterprise networks store a large amount of critical data (such as customer information, financial reports, business plans, etc.). Allowing unauthorized devices to connect is like leaving the company doors wide open.
Without certificate management, anyone with the Wi-Fi password can access the network and steal data. With certificate management, only devices with the “enterprise device identity certificate” can connect via Wi-Fi or VPN, acting as an “intelligent access control” that recognizes only “legitimate certificates.”
For example, a financial institution ensures that only employees’ work Android devices can access the internal network; outsiders without the device certificate cannot connect, preventing intrusion. This demonstrates why encrypted communication using certificates is essential to protect data during transmission.
Encrypted Communication: Prevent Data from Being Intercepted or Tampered With During Transmission
Data transmission is a crucial part of enterprise operations, and certificates serve as the “core guardians” ensuring transmission security. For example, a sales team uses Android phones to send daily sales reports containing sensitive customer and order information. Without SSL encryption, the data is sent in “plain text,” allowing hackers to intercept and steal it. With an SSL certificate, the data is encrypted into unreadable “garbled text,” and only the headquarters server with the private key can decrypt it. Even if a hacker intercepts the encrypted data, they cannot decipher its meaning.
Similarly, in a chain restaurant, store employees use Android devices to upload daily food procurement data. SSL ensures the data cannot be tampered with during transmission, preventing malicious changes that could cause financial losses. This highlights the importance of verifying data integrity to ensure received information remains unchanged.
Verify Data Integrity: Ensure Received Data Has Not Been Tampered With
In addition to preventing data interception, certificates also ensure that data is “not tampered with” during transmission, that is, they verify data integrity. The principle is: the certificate adds a “digital signature” to transmitted data, acting as its “fingerprint”—any modification changes the fingerprint. The recipient verifies the signature using the corresponding certificate: a match confirms data integrity, while a mismatch indicates tampering and requires retransmission.
This is critical in healthcare. For example, Android monitors transmit patients’ vital signs to the nurses’ station with a digital signature. If data is altered, the mismatch alerts staff. In logistics, digital signatures ensure delivery information uploaded from Android terminals remains accurate, avoiding tampering and disputes. This underscores the need for proper lifecycle management of Android certificates.
5Lifecycle Management of Android Certificates
Let us have a look at how the entire lifecycle of Android certificates is managed in different phases, starting from acquiring a certificate to revoking one, and everything in between.
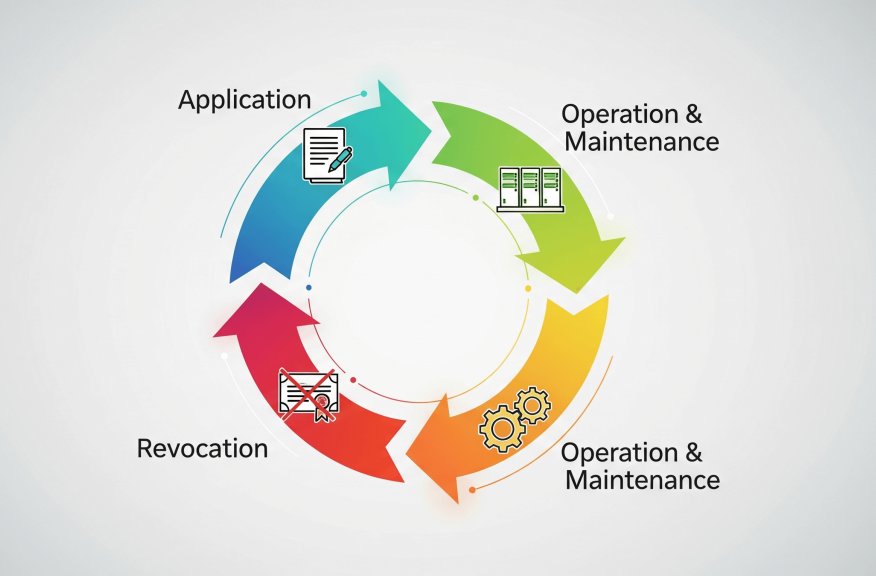
Phase 1: Application — Obtain a legitimate certificate from a CA
Certificates cannot be generated arbitrarily; they must be applied for from an authoritative CA (Certificate Authority). Enterprises should submit relevant qualification documents to the CA and only after approval can they obtain a legitimate and valid certificate.
Different scenarios require different types of certificates. For example, if an enterprise wants a device to access the VPN, it should apply for a device identity certificate; to secure an app, it needs to apply for a code signing certificate.
Phase 2: Deployment — Install the certificate on enterprise Android devices
After obtaining the certificate, it needs to be deployed to the corresponding Android devices. For small enterprises, manual installation may still be manageable, but for enterprises with dozens or hundreds of devices, manual deployment is inefficient and prone to errors (such as installing a certificate on the wrong or missing devices).
At this stage, using MDM tools like AirDroid Business enables IT staff to push certificates to hundreds of devices at once, completing deployment in minutes and greatly saving time.
Phase 3: Operation & Maintenance — Monitor certificate validity, update expired certificates, and troubleshoot certificate issues
Certificates all have a validity period (usually 1–3 years) and will automatically expire when the period ends, causing devices to stop functioning properly. Therefore, the core of the operation and maintenance phase is early warning and timely renewal.
IT personnel need to monitor the validity of all devices’ certificates in real time and complete updates before expiration. When devices encounter issues such as “certificate authentication failed” or “unable to connect to the network,” they must quickly troubleshoot the cause, whether it is certificate expiration, format errors, or a broken chain of trust.
Phase 4: Revocation — Revoke the certificate when a device is decommissioned or lost to prevent unauthorized use
When an Android device is decommissioned, lost, or when an employee leaves, the certificates on the device must be revoked promptly to prevent them from being stolen.
For example, when a courier at a logistics company lost a handheld terminal, the IT department immediately revoked the device’s certificate via the Airdroid Business backend. Even if the finder tried to access the corporate VPN, it would be blocked due to the certificate being invalid, protecting sensitive data. Neglecting revocation is like planting a time bomb in enterprise security.
It must be emphasized here: simply storing certificates without managing their lifecycle is equivalent to not managing certificates at all. Just like we don’t simply keep an ID card and ignore it, we also focus on the validity period and report if lost—the full lifecycle management of certificates is the key to ensuring security.
From application to revocation, AirDroid Business streamlines the entire certificate lifecycle. Automate deployments, monitor validity, and manage renewals effortlessly to maintain uninterrupted business operations.
6Conclusion
By understanding these different types of certificates, you can more clearly see their specific applications and importance in various enterprise scenarios. Together, they form a rigorous defense line for securing mobile devices. AirDroid Business, as a professional MDM solution, aims to automate this process, helping you say goodbye to cumbersome manual configurations and fundamentally ensuring the security of your enterprise mobile devices and data.







Leave a Reply.