Security and Compliance in Android Certificate Management
Ten Android-powered monitors at a private hospital failed to renew their expired certificates, resulting in the loss of encryption during transmission of patient data. Hackers intercepted the data via public Wi-Fi, leading to the leak of 500 patient records. Following the incident, regulatory authorities discovered that the hospital had not established a certificate lifecycle management mechanism, failing to comply with HIPAA (Health Insurance Portability and Accountability Act) requirements. The hospital was fined $800,000 and had its health insurance billing eligibility suspended for three months; a classic example of a "security vulnerability" leading to a "compliance crisis."

In another case, a payment chain, to save costs, failed to configure authoritative CA certificates for its Android point-of-sale (POS) devices, instead using self-signed certificates to process credit card transactions. A regulatory inspection determined the chain was non-compliant with PCI DSS (Payment Card Industry Data Security Standard).
The payment chain was fined $2 million and had its acquiring privileges suspended by credit card organizations, directly impacting the normal operations of nearly 1,000 stores. The core contradiction in these two incidents is that companies regard certificate management as a "technical detail" but ignore that it is both a "protective shield" for data security and an "entry ticket" for industry compliance. Without this link, both security and business will be in crisis.
1Security: How certificates strengthen the "three lines of defense" for Android devices
In light of the above real-life case studies, it shouldn’t be difficult to understand how certificates act as the spine for any organization’s data security and compliance. Below is a comprehensive explanation of what they are, how they work as a defence mechanism, and what critical job they’ve got to do.
Digital Certificates and PKI: The Cornerstone of Trust
Digital certificates are essentially the "electronic ID cards" of network entities. Issued by a trusted Certificate Authority (CA), they verify the identity of network entities (such as devices, servers, and applications), thereby establishing a foundation of trust between communicating parties.
At the core of this trust mechanism is the Public Key Infrastructure (PKI), a comprehensive framework comprising hardware, software, personnel, policies, and procedures for the creation, management, distribution, use, storage, and revocation of digital certificates.
In PKI, trust does not originate from a single entity, but rather a hierarchical, verifiable system, often referred to as a "Chain of Trust." The chain starts from the most trusted self-signed root certificate authority (Root CA) at the top level, passes through one or more intermediate certificate authorities (Intermediate CA), and ultimately points to the end-entity certificate, such as a website's server certificate or a device's client certificate.
Android devices are pre-installed with a trusted root certificate store, which acts as the "trust anchor" for the entire chain of trust. When a device receives an end-entity certificate, it traces the certificate's signature chain until it finds a root certificate in its trust store to verify its legitimacy.
The underlying technology behind this trust model is asymmetric cryptography, which uses a pair of mathematically related but underivable keys: a public key and a private key.
The public key can be shared publicly and used to encrypt data or verify digital signatures, while the private key must be kept strictly confidential and used to decrypt data or generate digital signatures. Digital certificates facilitate this complex encrypted communication process by confirming the legitimate ownership of the public key.
Line of Defense 1: Data Encryption – Ensuring Tight Transmission and Storage
Core role: Certificates are the "key foundation" for data encryption
Android devices handle customer information, transaction records, medical data, and other sensitive assets, and certificates are the core keys that protect these assets. Their encryption capabilities are primarily manifested in two ways:
- First, transmission encryption: SSL/TLS certificates convert communications between Android devices and enterprise servers into ciphertext. Even if the data is intercepted during transmission, hackers cannot decipher the content. For example, when a salesperson at a chain store uploads a customer order using an Android tablet, the SSL certificate encrypts the name, phone number, address, and other information on the order. This means hackers only see a string of random characters, rendering them unusable for malicious purposes.
- Second, storage encryption: The device identity certificate is bound to sensitive data stored locally on Android devices, creating a dual "certificate + data" protection. If the device is lost and without the corresponding certificate, even if someone cracks the device's lock screen password, they cannot access stored information like customer ID photos and contract scans.
A law firm once lost its Android office tablet, but thanks to the encryption of the device identity certificate bound to the local case files, no data was compromised.
Industry scenarios: Some businesses have an "unavoidable need" for encryption
The demand for data encryption in various industries is essentially an unavoidable demand for "business security". Take the following examples for better understanding:
- Healthcare scenarios: When nurses use Android handheld devices to record patient medication information and transmit examination reports, SSL certificates must be fully encrypted throughout the process. This not only protects patient privacy but also prevents medical accidents caused by data tampering. A maternity and child hospital once failed to enable certificate encryption, resulting in a newborn's blood type data being mistakenly altered during transmission, nearly leading to a blood transfusion error.
- Financial scenarios: When Android point-of-sale (POS) devices process credit card transactions, certificate encryption is a "bottom line requirement." A convenience store's POS device, due to expired certificates, allowed hackers to steal transaction data, resulting in the compromise of 200 customers' bank card information. The company ultimately paid hundreds of thousands of dollars in compensation to customers.
Secure Your Enterprise with AirDroid Business
Worried about security risks from expired or leaked certificates? AirDroid Business provides comprehensive lifecycle management to protect your data and ensure compliance.
Line of Defense 2: Authentication — Only “legitimate devices/applications” can access
Device identity verification: Prevent illegal devices from mixing in the network
Core resources like the company's intranet and VPN are like important company offices, requiring access only to private personnel. An Android device's identity certificate is the digital access card to these doors.
The authentication logic is simple: the company issues a unique identity certificate for each compliant Android device. When a device accesses the intranet or VPN, it presents this certificate to a server. The server verifies the certificate's legitimacy (whether it's issued by the company and whether it's valid). Only devices that pass verification can access the system.
The R&D department of an internet company uses this method to ensure that only Android development devices with identity certificates installed can access the code repository. Even if an outsider knows the VPN password, they can't hack without the certificate.
Conversely, the lack of device authentication can have disastrous consequences. A manufacturing company once failed to configure identity certificates for Android devices, allowing an outsider to connect to the workshop Wi-Fi using a personal phone and steal key process data from the production line. This directly led to a competitor seizing market share and resulting in nearly one million US dollars in losses.
Application Authentication: Blocking the Installation of “Risk Apps”
Applications on Android devices are like "visitors entering the company" and must undergo identity verification before being allowed in. A "code signing certificate" is a "digital pass" that verifies the application's identity.
Enterprise-developed ERP clients, customer management apps, and other applications must be "signed" with a code signing certificate before being deployed to Android devices. The device automatically verifies the signature during installation, allowing only verified "legitimate applications" to be installed. Unsigned pirated apps and malware are blocked. A restaurant chain once used this method to prevent employees from installing gaming apps on Android ordering devices. These apps not only take up device memory but can also carry viruses that steal order data.
Ignoring application authentication can quickly spread risks.
An e-commerce company's customer service Android device was infected with a Trojan horse after an employee privately installed an unsigned "price comparison tool," stealing the order information of 1,000 customers. The company was fined $100,000 by regulators.
Line of Defense 3: Preventing Man-in-the-Middle Attacks — Cutting Off “Data Hijacking” Paths
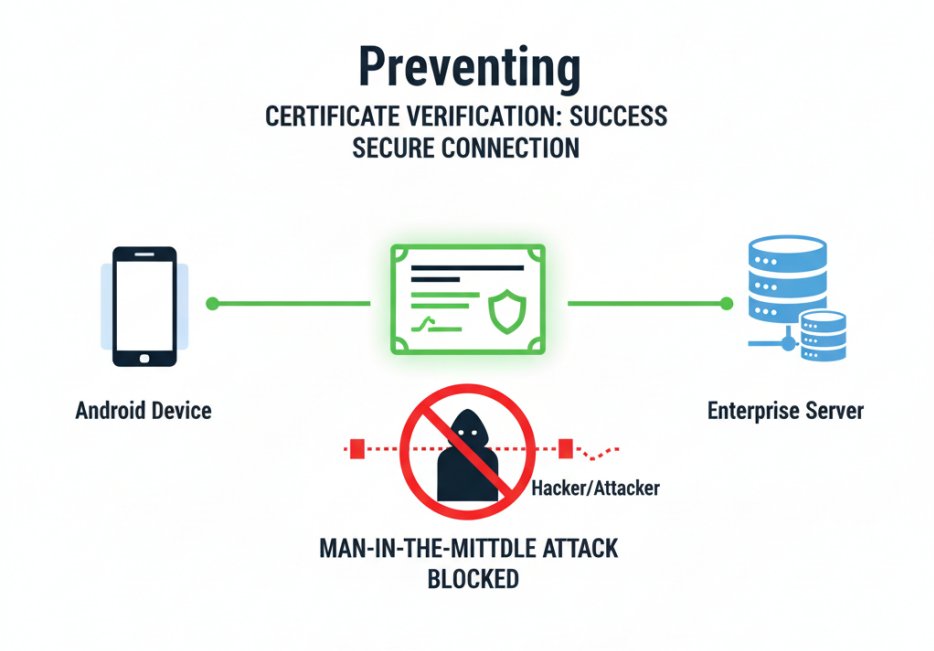
Attack Mechanism: How does the middleman "steal data"?
A "man-in-the-middle attack" is an invisible threat to Android devices on public networks. Hackers can disguise themselves as legitimate servers and establish a fake channel between the Android device and the real server, stealing or tampering with data.
For example, when an employee connects to the free Wi-Fi at an airport and opens the company's office automation system, the hacker might masquerade as the OA server, tricking the device into thinking it's connected to the "official platform." When the employee enters their account information and password and uploads data, this information is intercepted by the hacker and then forwarded to the real server, all without the employee or the company noticing. A sales representative at a foreign trade company experienced this attack, resulting in the hacker altering the quotations for five foreign trade contracts, causing the company to lose hundreds of thousands of dollars in orders.
The core vulnerability of this attack lies in the fact that, without certificate verification, Android devices cannot distinguish between the real server and the fake server, effectively falling prey to the trap.
The defensive role of certificates: verifying the “real identities” of both communicating parties
The certificate's digital signature feature fundamentally prevents man-in-the-middle attacks. It acts like a server's digital fingerprint, allowing Android devices to accurately identify the server.
The specific process is as follows:
- The enterprise server is configured with an SSL certificate, which contains the server's digital signature.
- When an Android device connects to the server, it first obtains the certificate and verifies the signature.
- If the signature matches the enterprise's preset signature, it indicates the server is the real server and communication is established.
- If not, the connection is immediately terminated and a risk alert is issued.
A consulting firm's employees frequently travel and process client data over public Wi-Fi. Thanks to the certificate's signature verification feature, they have never had their data hijacked. However, a competitor, which did not enable this feature, experienced employee and client information theft, resulting in a 20% increase in customer churn.
2Compliance: Certificate management is a must to meet industry standards
Without efficient and timely certificate management,you can’t think about meeting the strict industry requirements and this can lead to penalties and security risks. Let’s have a look at the core requirements of prominent international standards in different industries.
Healthcare Industry: HIPAA (Health Insurance Portability and Accountability Act) Certification Requirements
Core HIPAA Compliance Points for Android Devices
HIPAA is a "security red line" for the healthcare industry. Its requirements for Android devices center around "patient data protection," and certificate management is key to meeting these requirements:
- Explicit Requirement 1: Data Transmission and Storage Must Be Encrypted:
HIPAA stipulates that patient medical records, examination reports, medication records, and other data on Android devices must be encrypted using certificates when transmitted (e.g., from a monitor to a nurse's station) or stored (e.g., on a tablet to store medical records locally). The encryption algorithm must comply with industry standards.
- Explicit Requirement 2: Device Access Must Be Authenticated:
Android devices connected to medical systems (e.g., nurse tablets, mobile monitors) must verify their identity using certificates, prohibiting unauthorized access to prevent external devices from stealing patient data.
Violating these requirements can result in severe penalties for companies: HIPAA fines range from $100 per record to $15 million per violation, depending on the severity of the violation. Companies may also face suspension of their medical insurance and commercial insurance billing eligibility.
How Certificate Management Helps Enterprises Pass the Test
To pass HIPAA audits, medical companies must implement two key aspects of certificate management:
- First, deploy compliant certificates and maintain logs:
Each Android medical device must be equipped with an SSL certificate and identity certificate issued by a reputable CA to ensure data encryption and authentication. This includes recording the certificate's deployment time, device used, and operator, creating a comprehensive audit log. A tertiary hospital successfully passed its HIPAA audit on its first try, retaining logs for two years, far exceeding the "at least one year" requirement.
- Second, establish certificate lifecycle management:
regularly check certificate expiration dates and renew expiring certificates 30 days in advance. When devices are retired or decommissioned, certificates must be promptly deregistered to prevent reuse. A community hospital neglected this practice, resulting in 20 obsolete Android medical examination devices not having their certificates deregistered. These devices were then hacked by a recycler, leaking 1,000 pieces of residents' health data. The hospital was fined $3 million by HIPAA and lost its community medical service accreditation.
Achieve HIPAA Compliance with AirDroid Business
Ensure patient data protection with AirDroid Business. Our solution automates certificate management, helping you meet HIPAA requirements effortlessly.
Financial Industry: The “Hard Constraints” of PCI DSS (Payment Card Industry Data Security Standard)
Key PCI DSS Requirements for Android Payment Devices
PCI DSS, the financial payment industry's security standard, imposes strict restrictions on Android devices that process credit card transactions (such as POS terminals and mobile cash register tablets). The core requirement is certificate management:
- Core Clause 1: Device Identity Must Be Uniquely Verified: Each Android payment device must have a unique identity certificate issued by a third-party, authoritative CA; self-signed certificates are prohibited. When a device connects to the payment system, it must undergo certificate verification to prevent counterfeit devices from accessing and stealing transaction data.
- Core Clause 2: Transaction Data Transmission Must Be Encrypted: Sensitive information such as credit card numbers, expiration dates, and CVV codes must be encrypted using an SSL/TLS certificate when transmitting from the Android payment device to the payment gateway, and the encrypted link must remain uninterrupted.
PCI DSS penalties are equally severe: non-compliant businesses will be fined $5,000 to $1 million per month by credit card organizations, and in serious cases, their acquiring privileges may be suspended—a tantamount to a loss of revenue for businesses that rely on credit card transactions.
Compliance implementation of certificate management
Meeting PCI DSS Requirements for Certificate Management
To meet PCI DSS requirements, financial institutions must implement two strict requirements in certificate management:
- Strictly select certificate types:
Third-party, authoritative CA certificates (such as WoSign and Symantec) must be used; self-signed certificates are prohibited. A supermarket chain, in an effort to save costs, used self-signed certificates for its Android POS devices. This practice was discovered during a PCI DSS audit and resulted in a $1.5 million fine and a three-month suspension of its acquiring privileges by Visa and MasterCard. During this period, the store's cash transaction rate soared from 30% to 70%, leading to significant customer loss.
- Strictly verify certificate status:
Monthly verification of the validity and integrity of certificates for Android payment devices is conducted, generating a verification report. If a certificate is found to have been tampered with or leaked, it must be frozen and replaced within 24 hours. A bank's Android mobile cash registers, due to IT staff failing to promptly detect certificate tampering, resulted in the theft of 50 credit card transaction data. The bank ultimately incurred 800,000 yuan in customer compensation and suffered a PCI DSS rating downgrade from "A" to "C."
General Compliance: GDPR (General Data Protection Regulation) "Certificate Link"
GDPR's core requirements for Android device data
GDPR is a "compulsory compliance course" for cross-border enterprises. Its core principle is "user data security and traceability"—and certificate management is a key means of achieving this "traceability."
GDPR explicitly requires that when enterprises process user data (such as customer contact information and spending records stored on employees' Android devices), they must record "who accessed what data, when, and through what device." Certificate management, through a combination of "device certificates + operation logs," precisely meets this requirement. Every certificate operation on every Android device (such as using a certificate to decrypt data or access systems) is recorded, forming a traceable audit trail.
Failure to meet this requirement can lead to hefty fines: GDPR fines can reach up to 4% of a company's global annual revenue or €20 million (whichever is higher), a burden that any company would find unbearable.
Compliance Practice: Certificate Logs Become “Audit Evidence”
To pass GDPR audits, companies must include certificate logs in the "compliance evidence chain." Specifically, they must ensure two key aspects:
- First, complete log information:
Logs must include the operator's name, operation time, device ID, certificate type, and operation details (e.g., deployment, update, or revocation). Logs must also be encrypted and stored to prevent tampering. A cross-border e-commerce company's Android customer service devices, with complete certificate operation logs, were audited in just three days during a GDPR audit, with no issues identified.
- Second, ensure log retention:
GDPR requires user data logs to be retained for at least one year, with some industries (such as finance) requiring three years. A cross-border consulting company was once required to rectify its certificate logs during a GDPR audit because it only retained them for six months. During this rectification period, it was unable to provide services to EU clients, resulting in millions of yuan in lost revenue.
3Risk Warning: Three Serious Consequences of Poor Certificate Management

Keeping in mind the above three-layered defence provided by proper certificate management, poorly managed certificates by enterprises can lead to serious consequences.
Consequence 1: Certificate Expiration – Business Interruption and Security Vulnerabilities
Certificates have an expiration date (usually 1-3 years), after which they automatically lose their encryption and authentication functions, leading to two direct risks:
- First, business interruption: Android devices cannot access VPNs/intranets or transmit data, sales tablets cannot check inventory, kiosks cannot upload sales reports, and medical devices cannot transmit patient data, bringing business to a standstill. A chain of pharmacies, with 20 Android cash registers, was unable to access the medical insurance system due to expired certificates. The store was closed for two hours, resulting in tens of thousands of dollars in lost revenue.
- Second, security vulnerabilities: Expired certificates cannot encrypt data, rendering the devices "naked". Data transmission is vulnerable to interception, and device access lacks authentication, making them easily compromised by hackers. A medical clinic's Android health examination devices, due to expired certificates, had 500 resident health examination reports stolen during transmission, resulting in a $1 million fine from regulators.
A supermarket chain experienced peak customer traffic before the Lunar New Year holiday when 200 Android cash register devices suddenly experienced a collective internet outage. Investigation revealed that the SSL certificates for all devices had expired simultaneously, preventing them from accessing the payment system. Because the supermarket hadn't provided advance warning, the IT team had to manually update the certificates device by device, resulting in a four-hour store closure.
This incident directly resulted in two major losses:
- First, lost revenue, resulting in a 500,000 yuan loss due to missed peak customer traffic
- Second, customer churn, with many customers unable to check out and opting for other supermarkets, leading to a 15% drop in post-holiday foot traffic. The root cause of this was the company's reliance on Excel to record certificate expiration dates, resulting in a missed "collective expiration" notification.
Consequence 2: Leaked certificates – the key to hacking
While certificate leaks may seem hidden, they are often caused by management negligence:
- First, unencrypted local storage: IT personnel store certificate files on unencrypted computer hard drives or USB drives, which can then be compromised after the device is lost. In one case, an IT employee at a company accidentally lost a USB drive containing the identity certificates of 100 Android devices. Hackers used these certificates to access the company's intranet and steal 200 customer contracts, ultimately costing the company 3 million yuan in compensation.
- Second, lax permission control: Failure to restrict access rights to certificates allows unauthorized personnel (such as outsourced employees and interns) to copy them at will. In one case, an outsourced employee at a financial institution copied the certificates of an Android POS device while IT staff were unprepared and resold them to a third-party company, resulting in the compromise of 1,000 credit card transaction records and a $5 million fine imposed on the institution under PCI DSS regulations.
The harm of certificate leaks spreads from the data level to the system level:
At the data level, hackers can use leaked certificates to decrypt sensitive data stored on Android devices e.g. medical records for healthcare companies, bank card information for financial institutions, and customer data for retail businesses, all potentially becoming targets.
A health technology company was fined $8 million under HIPAA due to a certificate leak, resulting in the sale of 10,000 pieces of user health data. The company also lost its license to operate in the US market.
At the system level, hackers can use leaked device identity certificates to access corporate intranets and tamper with business data, changing transaction amounts on Android POS devices, deleting operation records on production equipment, and injecting viruses to paralyze servers.
A manufacturing company once suffered a certificate leak, allowing Android monitoring devices on its production line to be hacked and production data to be tampered with, resulting in batches of defective products and losses of nearly 10 million yuan.
Consequence 3: Poor management – compliance fines and license revocation
The direct consequence of poor certificate management is severe fines from regulators, with fines varying across different industries:
- Healthcare (HIPAA): Violations are categorized into four levels, with fines up to $15 million per violation. A private hospital was fined $12 million under HIPAA for leaking 100,000 pieces of patient data due to unencrypted Android medical device certificates.
- Financial (PCI DSS): Fines range from $5,000 to $1 million per month, with cumulative penalties depending on the duration of the violation. A payment company was fined $4 million for six months of poor Android POS device certificate management violations.
- Cross-border (GDPR): Fines up to 4% of a company's global annual revenue, or €20 million. A cross-border e-commerce company was fined €8 million (approximately 60 million RMB) for incomplete Android device certificate logs and GDPR non-compliance. For small and medium-sized enterprises, these fines may directly lead to a "break in the capital chain" for large enterprises, they will also seriously affect profits and cash flow.
Even more formidable than fines are the indirect losses caused by poor certificate management:
First, business license revocation: Medical companies may lose their medical insurance and commercial insurance settlement eligibility, financial companies may lose their acquiring rights, and cross-border businesses may be restricted from entering target markets.
A community hospital's medical insurance eligibility was suspended for six months due to non-compliant certificate management. During this period, it experienced a 60% patient churn rate and was ultimately forced to close.
Second, brand trust collapses: After data breaches and compliance fines are exposed, customers lose trust in a company and choose competitors.
A bank's Android mobile banking certificate vulnerability led to the leakage of customer information, causing a sharp drop in brand trust, a 25% increase in customer churn within six months, and a 40% drop in wealth management product sales.
3Conclusion: Best Practices: Building a Robust Android Certificate Management Strategy
Automation Strategy Implementation: Scale and Security
To effectively address these challenges and manage them at scale, companies must abandon manual processes and adopt strategic, automated solutions.
Centralized management using MDM/UEM is a top strategic initiative. MDM or UEM solutions provide a unified console where IT administrators can remotely and automatically manage certificates for their entire Android device fleet. This allows administrators to deploy certificates to hundreds or thousands of devices in bulk with a single click, eliminating the need for manual user intervention.
MDM platforms also provide real-time monitoring capabilities, allowing administrators to audit the certificate status of each device to ensure validity and remotely revoke suspicious certificates.
Automating the certificate lifecycle is key to realizing the full potential of MDM/UEM platforms. Automation tools, such as the Simple Certificate Enrollment Protocol (SCEP), can streamline certificate application, issuance, deployment, renewal, and revocation, significantly reducing IT burden and human error.
For example, the system can automatically alert administrators when a certificate is about to expire, even automating renewal and deployment before expiration.
Technical and operational best practices
In addition to centralized management at the strategic level, the following best practices must be adhered to at the technical and operational levels:
Adopt strong cryptographic standards and algorithms: Always use modern, powerful cryptographic algorithms and protocols, such as TLS 1.3, the SHA-2 family, and AES-256. Notably, as of Android 10, certificates signed with the SHA-1 algorithm are no longer trusted by default.
Ensure traceability and auditability: Maintaining a complete certificate inventory and audit logs is crucial. This is not only a compliance requirement but also key to detecting anomalies and rapidly responding to security incidents. The certificate inventory should include metadata such as the certificate's location, validity period, and issuer to facilitate ongoing monitoring and compliance audits.
Address the trend toward shorter certificate validity periods: The industry is gradually reducing certificate validity periods from 398 days to 47 days. This trend makes manual management nearly impossible. Therefore, automated certificate management has evolved from a "nice to have" to a "must have."
Transform Your Certificate Management with AirDroid Business
Ready to enhance security and compliance? AirDroid Business provides a comprehensive MDM solution for automated certificate management.







Leave a Reply.