Securing Kiosk Mode with Certificates
- 1 : The "security vulnerability" of Kiosk Mode: The hidden risks of devices in public places
- 2 : Why is a certificate required for Kiosk Mode? — The security imperative for devices in public places
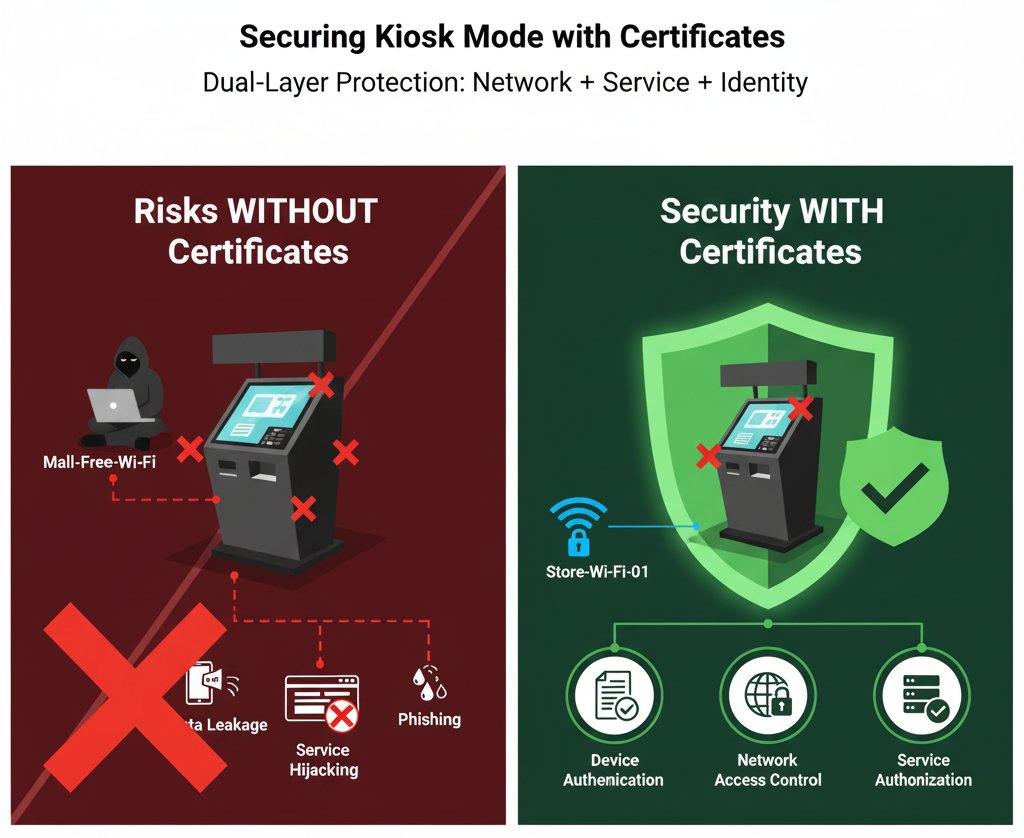
- 3 : The core application of certificates in Kiosk Mode: dual-layer protection of network + service
- 4 : Best Practices for Kiosk Mode Certificate Management: Balancing Security and Efficiency
- 5 : Conclusion: Certificates upgrade Kiosk Mode from "functional limitations" to "secure closed loop"
Part 1: The "security vulnerability" of Kiosk Mode: The hidden risks of devices in public places
Kiosk devices in public places are always at a high risk of abuse. These risks can even lead to security breaches and disrupted services. Let us have a look at some of the real-world security vulnerabilities of kiosk devices and how to mitigate them.
Common security risks of kiosk devices
Real Case: From "Data Leakage" to "Service Hijacking" Risks
A chain shopping mall deployed shopping guide kiosks in 20 stores, allowing customers to search for product information, leave contact information, and schedule in-store visits. However, a hacker set up a malicious network inside the mall called "Mall-Free-Wi-Fi." Passersby mistakenly connected the kiosks to the network. Over a three-day period, 1,200 customer phone numbers and reservation information were intercepted, and some of this information was used to send spam marketing text messages. This incident resulted in nearly 50 complaints to the mall, and a sharp drop in brand trust.
An even more serious case occurred at an airport: Because the check-in kiosk had unrestricted network access, hackers hacked into the device through the airport's public Wi-Fi and tampered with the flight information system, changing a "flight delayed by one hour" to "flight canceled."
This led to nearly 200 passengers gathering at the check-in counter to protest their rights, forcing the airport to scramble personnel to rectify the situation and causing operational disruption. These crises exposed a core security weakness of Kiosk Mode:
Kiosk Mode devices are often located in public places like shopping malls, airports, and tourist attractions, without 24/7 staff. They face both the physical risk of passersby modifying network settings and the cyber threat of remote hacker attacks. Traditional Kiosk Mode devices only restrict access to the device interface (for example, prohibiting exiting the query page or installing apps). This is like locking the device's door but leaving the network window open, completely failing to protect against network-layer attacks.
Certificates are a "security patch" for Kiosk Mode
The Irreplaceability of Certificates: From “Functional Limitation” to “Authentication + Access Control”
If Kiosk Mode's functional limitations are like "guardrails to prevent unauthorized access," then certificates are like "anti-theft doors to prevent intrusion."
Traditional security measures only address the issue of users preventing unauthorized device operation, but fail to address issues like devices connecting to the wrong networks or accessing the wrong services. Certificates, on the other hand, provide a strong security barrier for Kiosk devices through two core capabilities:
Device authentication: issuing a "digital ID" to each kiosk ensures that only legitimate devices are recognized by the enterprise backend.
Network/service authorization: locking down the networks and services a kiosk can connect to, eliminating the risk of connecting to malicious Wi-Fi networks or visiting phishing websites.
For businesses that rely on kiosk devices for business operations, certificates aren't an optional security upgrade; they're essential infrastructure. The following article will detail why certificates are essential for Kiosk Mode and how to implement security protection using certificates.
Secure Your Kiosk Devices with AirDroid Business
Enhance your kiosk security with AirDroid Business. Ensure only authorized network access and service use with our robust certificate management.
Part 2: Why is a certificate required for Kiosk Mode? — The security imperative for devices in public places
If you wonder what benefit these certificates bring to the overall security of kiosk devices, they act like a strong barrier against intruders. Here’s why you can’t do without them.
1Risk 1: “Lose-Control Network Access” Due to Physical Accessibility
Scenario pain point: Anyone can modify the Kiosk's network settings
The physical accessibility of kiosk devices poses one of the greatest security risks. In stores, exhibitions, and other settings, these devices are often placed in open areas. Passersby can simply long-press the device's power and volume buttons to enter Android's "setup mode" and modify the Wi-Fi connection.
A customer once pranked a milk tea chain's cashier kiosk by connecting it to their phone's hotspot, preventing the kiosk from accessing the store's order system. For 30 minutes, checkout was unavailable, and nearly 30 customers were lost from the queue.
Even more dangerous is malicious modification: At one exhibition, an inquiry kiosk was hacked and connected to a fake "Expo-Admin-Wi-Fi." The exhibitor list and visitor registration information transmitted by the device were intercepted in real time. Within two days, the contact information of 50 exhibitors was leaked, forcing the exhibition organizer to pay the exhibitors hundreds of thousands of dollars in compensation.
The root of these problems is that Kiosk devices allow network settings to be modified by default, and manual supervision is unrealistic. Simply "posting warning signs" or "hiding the settings button" cannot fundamentally solve the problem.
The defensive role of certificates: Locking down the "trusted network" and denying unauthorized access
The advent of certificates enables kiosk devices to recognize only designated Wi-Fi networks. The principle is simple: a dedicated Wi-Fi certificate is deployed to the kiosk device. This certificate contains the SSID of the company's designated Wi-Fi network (e.g., "Store-Wi-Fi-01") and a digital signature. When the device attempts to connect to a Wi-Fi network, it automatically verifies the network's SSID and signature. Only Wi-Fi networks that exactly match the certificate are successfully connected; other networks (including malicious Wi-Fi networks and mobile hotspots) are rejected.
After a restaurant chain deployed Wi-Fi certificates for 500 of its kiosks, even when someone accessed the settings interface and attempted to connect to other networks, the device would display a "Certificate verification failed, unable to connect" message, preventing any connection. In the past year, the company has experienced no business interruptions due to misconnecting to the wrong network, and the IT team's time spent troubleshooting network issues has been reduced from eight hours per month to one.
Simplify Certificate Management with AirDroid Business
Streamline your certificate deployment and management with AirDroid Business. Protect your kiosks from unauthorized access effortlessly.
2Risk 2: “Service Access Chaos” Caused by Network Openness
Scenario pain point: Kiosk may access unauthorized services, causing functional abnormalities
Even if a kiosk is connected to the correct network, it can still experience malfunctions or data leaks if service access isn't restricted. A scenic spot's ticketing kiosk encountered such an issue: although the device was connected to the attraction's dedicated Wi-Fi, because service access wasn't restricted, a visitor mistakenly opened a browser and visited a phishing ticketing website. After paying, the visitor found they couldn't collect their tickets, forcing the attraction to issue an urgent refund and apology, impacting the experience of nearly 100 visitors.
Even more serious is service hijacking: Because a hotel's self-check-in kiosk could access any service, hackers hijacked the network and redirected the kiosk's "identity information upload service" to their own servers. Within three days, 80 guests' ID photos and phone numbers were stolen. The hotel not only faced fines from regulators but also lost nearly 20% of its repeat customers.
These issues demonstrate that it's not enough to simply manage "what network" a user connects to; it's also crucial to manage "what they use the network for." Kiosk devices must only access services that support core business operations; all other irrelevant services must be blocked.
The defensive role of certificates: only authorize "trusted services" and block illegal requests
Certificates undergo "service digital signature verification," ensuring that kiosks only recognize "enterprise-authorized services." Specifically, the enterprise configures SSL certificates for core services the kiosk needs to access (such as ticketing systems, payment gateways, and check-in systems). These certificates contain the service's digital signature. When the kiosk attempts to access a service, it first verifies whether the service's signature matches the certificate. If so, access is permitted; otherwise, it is blocked.
Airport check-in kiosks are a prime example: airlines configure their check-in systems with dedicated SSL certificates. Kiosk devices can only access official check-in services using this certificate, denying access to phishing check-in websites or unrelated services (such as third-party websites for flight status updates). After adopting this solution, one airport has eliminated passenger confusion caused by "accessing the wrong service," and the number of check-in kiosk failures has dropped from five per month to zero.
3Risk 3: Identity theft caused by device sharing
Scenario Pain Point: Illegal devices disguised as kiosks access enterprise systems
Enterprise kiosks typically access backend systems (such as inventory management and order statistics) to obtain data. Without device identity verification, hackers can forge the kiosk's device information and impersonate legitimate devices to access the system. A retail company's store kiosk experienced this type of attack: hackers used technical means to modify their own tablet device information, posing as a store kiosk and accessing the company's inventory system. They inflated the inventory of 100 popular items, misleading headquarters into believing they had sufficient inventory and failing to restock them, ultimately resulting in tens of thousands of dollars in lost revenue due to stockouts.
Even more dangerous is data tampering: The backend system of a logistics pickup kiosk failed to verify the device's identity. After posing as a kiosk, hackers altered the pickup status of 20 packages (changing "not picked up" to "picked up"), preventing customers from picking up their packages. The logistics company had to compensate customers for their losses and re-deliver, incurring significant additional costs.
The core of these risks lies in the company's inability to distinguish legitimate devices—relying solely on easily tampered information like device model and serial number to ensure that the kiosk connecting to the system is genuine.
The defensive role of certificates: verifying the “legitimate identity” of the Kiosk
A device identity certificate is like a kiosk's "digital ID," unique and tamper-proof. Enterprises issue a unique certificate for each kiosk. This certificate contains the device's unique identifier (such as the IMEI number) and the company's digital signature. When a kiosk attempts to access backend systems, the system requires the device to present this certificate, which is only allowed after verification.
After a logistics company deployed device identity certificates for 300 pickup kiosks, hackers repeatedly attempted to impersonate the devices and access the system, but were unable to provide legitimate certificates. In the past year, the company has not experienced a single data tampering or inventory disruption caused by identity theft, and the security incident rate for backend systems has decreased by 95%.
Part 3: The core application of certificates in Kiosk Mode: dual-layer protection of network + service
Certificates not just prevent unauthorized network access but also ensure uninterrupted service, letting the devices do ‘only’ what they’re meant to do.
1Application 1: Network Access Control – Ensuring Kiosk Connects Only to Trusted Wi-Fi
Core Goal: From "Connecting to the Internet" to "Connecting Only to Trusted Networks"
For kiosk devices, connecting to the right network is the first step to security. Traditional Wi-Fi whitelisting solutions (manually setting only specific Wi-Fi networks) have two major drawbacks: first, the whitelist can be easily modified through the settings interface; second, manual whitelist maintenance is extremely inefficient when there are many devices (100 devices would require two people a day).
The certificate solution, on the other hand, uses Wi-Fi certificate binding to enforce the association of devices with trusted Wi-Fi networks. This eliminates the need for manual whitelist maintenance; devices automatically reject unauthorized networks, fundamentally solving the problem of connecting to the wrong network.
Application value: Reduce network management costs and prevent malicious access
By implementing Wi-Fi access control through certificates, companies no longer need to assign personnel to regularly check the network connection status of kiosks, nor do they have to worry about passersby maliciously modifying network settings.
After a retail chain configured Wi-Fi certificates for 200 store kiosks, network failure rates dropped from 10 per month to zero. The IT team no longer needs to make on-site visits to resolve "wrong network connection" issues, resulting in a 120-fold increase in management efficiency.
2Application 2: Service Access Restriction - Ensure Kiosk only accesses “trusted services”
Core goal: From "accessible" to "access only authorized services"
The core value of kiosk devices is to provide specific services (such as shopping guides, ticket purchases, and check-in). Accessing unrelated services not only disrupts the user experience but also poses security risks. The certificate solution uses "service certificate verification" to ensure that kiosk devices can only access enterprise-authorized services, eliminating the problem of "accessing the wrong service."
Application scenario: covering different types of Kiosk devices
Certificate control can be implemented specifically based on kiosk usage patterns:
Kiosks with built-in apps (such as retail self-checkout kiosks): Certificates restrict launches to only company-signed apps and ensure that apps can only access core services with certificates (such as payment gateways), preventing malicious apps or unauthorized services from accessing them.
Browser-based kiosks (such as scenic spot inquiry kiosks): Certificates restrict browser access to only trusted websites (such as the scenic spot's official website and ticketing system), blocking phishing websites and irrelevant pages.
After implementing certificate control for browser-based kiosks at one scenic spot, the invalid access rate (users attempting to access non-scenic spot websites) on inquiry devices dropped from 30% to 0, and the success rate of visitor inquiry functions increased to 98%.
Part 4: Best Practices for Kiosk Mode Certificate Management: Balancing Security and Efficiency
Let us now have a look at how to get the best out of kiosk certificates so that there aren’t any loopholes left.
1Practice 1: "Linked Deployment" of Certificates and Kiosk Mode
Core value: Avoid the risk of asynchronous deployment
When managing devices manually, enterprises often face the problem of Kiosk mode and certificate deployment being out of sync:
First enabling Kiosk mode on devices, then manually installing certificates. This can lead to 15 out of 100 devices missing certificates, resulting in devices being unable to connect to the internet or access services, necessitating IT personnel's on-site visits and extremely inefficient.
AB's "Linked Deployment" completely solves this problem: when creating a provisioning template, the required certificates (Wi-Fi certificate, service certificate) are pre-associated. When the device applies the provisioning template and enables Kiosk mode, the certificates are automatically and silently installed—removing manual intervention and reducing the missed installation rate to zero.
When an exhibition company deployed 200 query kiosks, linked deployment enabled them to automatically enable Kiosk mode and install certificates upon device activation. From unboxing to normal use, the process took only 5 minutes, allowing a single IT staff member to complete the entire deployment in one day, achieving a 5x improvement in efficiency compared to manual deployment.
2Practice 2: Automated Management of the Certificate Lifecycle
Core requirement: Avoid functional interruption caused by Kiosk certificate expiration
Certificates have expiration dates. If they're not renewed upon expiration, kiosk devices may suddenly lose access to the internet or services.
For example, an airport check-in kiosk once experienced certificate expiration, leaving 10 devices unusable during the morning rush hour, causing disruption to passenger queues.
Automated lifecycle management enables features such as certificate expiration alerts, automatic updates during off-peak hours, and phased testing and verification. This eliminates the need for manual monitoring of expiration dates and the worry that updates might impact business operations.
After implementing this solution across 500 of a chain's store kiosks, the company has experienced no issues due to expired certificates for nearly a year, and the time IT staff spend on certificate updates has been reduced from 16 hours per month to just one.
3Practice 3: Abnormal Monitoring and Rapid Stop-Loss
Core role: timely detection and resolution of certificate risks
Even if certificates are configured correctly, verification may still fail due to network fluctuations or device failures. Real-time monitoring of certificate status (such as validity, expiration, and verification failures) allows for quick detection of anomalies. Automatic alerts can also be set to ensure IT staff receive prompt notifications and address them, preventing further risk.
At one exhibition, 10 of 20 query kiosks failed verification due to a Wi-Fi router certificate update. Thanks to real-time monitoring and alerts, IT staff were notified within one minute and quickly reconfigured the certificates. All devices were back online within five minutes, ensuring no disruption to the exhibition experience.
Certificates upgrade Kiosk Mode from "functional limitations" to "secure closed loop"
For kiosk devices deployed in public places, security isn't an "add-on requirement" but a "prerequisite for business operations." Certificates provide a complete security loop for Kiosk Mode through three core benefits:
- Network Security: Locks down trusted Wi-Fi, preventing malicious network access and ensuring devices connect to the right network;
- Service Security: Authorizes only trusted services, blocking phishing and invalid access, ensuring devices access the right services;
- Identity Security: Verifies the legitimate identity of devices, preventing unauthorized access and ensuring enterprise recognition.
With tools that support certificate management, enterprises can easily implement these security measures, achieving the goals of reducing costs, improving efficiency, and ensuring security without complex operations.
If your enterprise also uses kiosk devices and faces the security risk of connecting to the wrong network or accessing the wrong service, consider starting with certificate protection to strengthen the security of devices in public places, ensuring that kiosks provide convenient user services while maintaining stable and secure operation.
Achieve Complete Security with AirDroid Business
Implement a secure closed-loop system for your kiosks. Reduce costs, improve efficiency, and ensure security with AirDroid Business.
Part 5: Conclusion: Certificates upgrade Kiosk Mode from "functional limitations" to "secure closed loop"
For kiosk devices deployed in public places, security isn't just an "add-on requirement" but a "prerequisite for business operations." Certificates provide a complete security loop for Kiosk Mode through three core benefits:
- Network Security: Locks down trusted Wi-Fi, preventing malicious network access and ensuring devices connect to the right network;
- Service Security: Authorizes only trusted services, blocking phishing and invalid access, ensuring devices access the right services;
- Identity Security: Verifies the legitimate identity of devices, preventing unauthorized access and ensuring enterprise recognition.
With tools that support certificate management, enterprises can easily implement these security measures, achieving the goals of reducing costs, improving efficiency, and ensuring security without complex operations. If your enterprise also uses kiosk devices and faces the security risk of connecting to the wrong network or accessing the wrong service, consider starting with certificate protection to strengthen the security of devices in public places, ensuring that kiosks provide convenient user services while maintaining stable and secure operation.







Leave a Reply.