Key Features of MDM Certificate Management: A Practical Checklist

- 1 : The Need for Automated Certificate Management
- 2 : Core Feature 1: Centralized Deployment and Management
- 3 : Core Feature 2: Automated Lifecycle Management
- 4 : Core Feature 3: Policy-Driven Adaptation
- 5 : Core Feature 4: Monitoring and Alerts
- 6 : Core Feature 5: Seamless Security Integration
- 7 : Core Feature 6: Multi-Scenario Linkage
- 8 : Three Pitfalls to Avoid in MDM Tool Evaluation
- 9 : Choosing the Right MDM Tool
The Need for Automated Certificate Management
Why Manual Management Persists

A retail chain purchased an MDM tool to manage certificates for 500 kiosk devices, but discovered the tool didn't support batch deployment. The IT team still had to plug in each device and transfer certificates, requiring three days of overtime to complete a single update. A medical company's MDM tool lacked certificate expiration warnings and relied entirely on Excel to record validity periods. Last year, a missed update caused the certificates of 20 monitors to expire, leaving the devices disconnected from the internet and unable to upload patient data. The company was warned by regulators.
The core contradiction in these dilemmas is that when enterprises choose MDM, they only focus on the superficial promotion of "being able to manage certificates" and fail to grasp the "key functions that solve actual pain points" (including the linkage between certificates and business functions). In the end, the tools become "useless", and the inefficiency and risks of manual management still exist.
How This Checklist Fits Your Needs
This article's "6 Core Features + 3 Pitfalls to Avoid" isn't just a general technical overview, but a summary of real-world challenges experienced by thousands of businesses. Each feature description is accompanied by quantifiable evaluation criteria, allowing you to directly compare your MDM tool's performance against these criteria. Whether you're an IT administrator at an SMB or an architect at a mid- to large-scale enterprise, this list will help you choose an MDM tool that's practical and truly user-friendly.
Core Feature 1: Centralized Deployment and Management

Efficient Certificate Distribution
When manually managing certificates, 100 devices would require three IT staff members to work overtime for one day, and it is easy for missed installations or wrong installations to occur. However, MDM tools that support batch deployment can shorten this process to 10 minutes and can be completed by one person. The core is to replace repetitive manual operations with "centralized control + automated push."
For companies with over 50 devices, this feature is essential. For example, a logistics firm with 300 handhelds uses AirDroid Business’s batch deployment to update all devices in 15 minutes during monthly certificate renewal, saving eight hours compared to manual work.
3 Key Metrics for Deployment Capability
Metric 1: Batch Distribution
When choosing a tool, enterprises should first determine if it can support their device deployment volume. This is specifically based on three criteria:
- Number of devices supported in a single batch: Small and medium-sized enterprises should choose a tool that supports at least 500 devices. Medium and large enterprises (1,000+ devices) should use tools with unlimited scalability, such as AirDroid Business, which supports deployments of tens of thousands of devices without limits.
- Deployment time: A deployment time of 100 devices in 10 minutes or less is considered acceptable.
- Support for compressed file uploads: If an enterprise has multiple certificates (e.g., Wi-Fi certificates, VPN certificates), confirm that the tool supports batch upload of compressed zip files to avoid uploading the same file repeatedly.
Metric 2: Zero-Touch Support
When new devices arrive, certificates are automatically installed upon device power-up, eliminating the need for IT personnel to visit or remotely control them. This is the value of "zero-touch deployment," especially suitable for multi-regional enterprises. Two key points should be considered during evaluation:
- Activation-as-deployment: Once a device is connected to the internet, when activated using a "zero-touch activation code" through tools like AirDroid Business, it automatically identifies the device's group, matches the corresponding certificate, and silently installs it, eliminating the need for any employee interaction.
- Offline reinstallation: If the device is offline during activation, can the tool automatically detect "missing certificates" and reinstall the certificates after going online? A cross-border e-commerce firm with 10 overseas warehouses in Germany and France used zero-touch deployment for 200 new Android scanners. From unboxing to use took 5 minutes, with no IT staff sent abroad, saving 120,000 yuan in travel costs.
Metric 3: Flexibility
Enterprises often need to deploy certificates during non-business hours (e.g., retail stores to avoid network outages during business hours, hospitals to avoid peak patient visits). The flexibility of the tool directly impacts business continuity. During the evaluation, focus on:
- Scheduled deployment: Can you set a specific time (e.g., 2 AM) for automatic execution? AirDroid Business supports scheduled tasks with hourly and minute-by-hour accuracy, and you can also set recurring deployments (e.g., update at midnight on the 1st of each month)?
- Batched deployment: When deploying over 1,000 devices, a single push can cause network congestion. Confirm whether the tool supports proportional batching (e.g., rolling out to 10% of devices first, then rolling out to the remaining 90% if no issues are encountered).
Centralize Your Operations with AirDroid Business
Need efficient certificate distribution? AirDroid Business supports batch deployment for thousands of devices, ensuring quick and error-free updates.
Core Feature 2: Automated Lifecycle Management
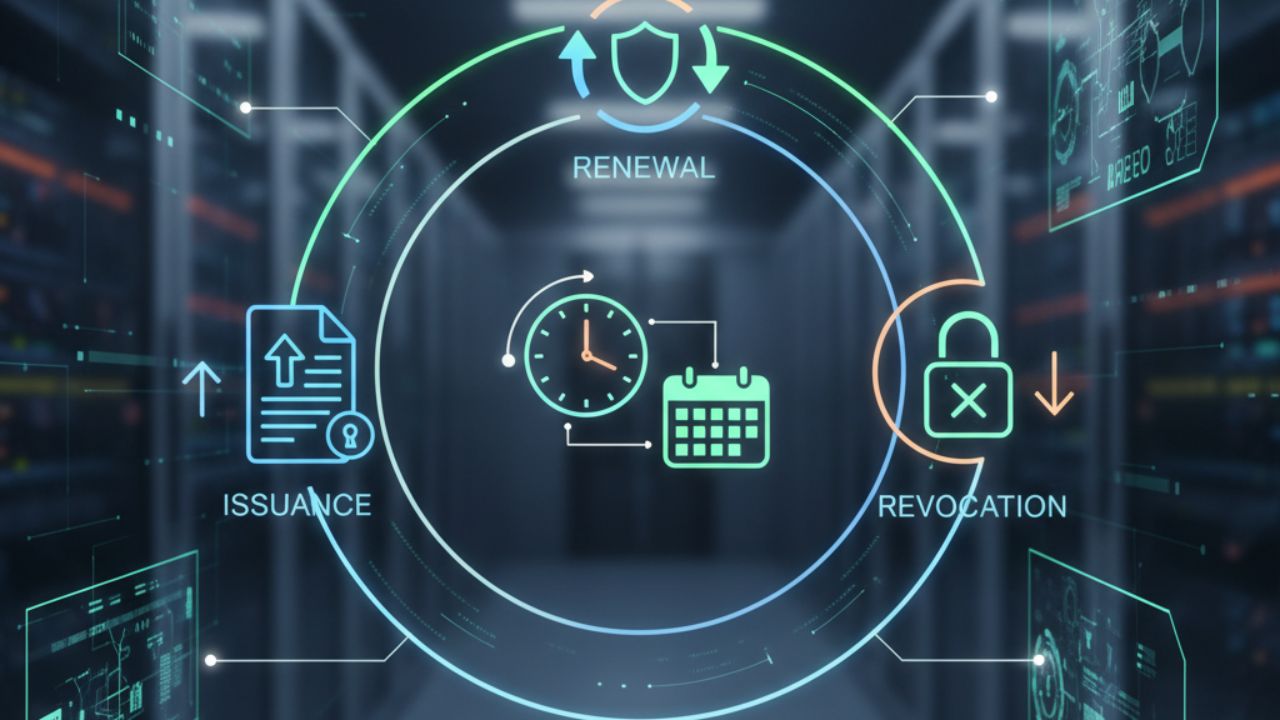
Full Coverage of Issuance, Renewal, Revocation
The certificate lifecycle is like an employee's journey from joining, to being employed, to leaving. Every step must be carefully considered: issuance corresponds to onboarding, renewal corresponds to contract renewal, and revocation corresponds to resignation. Manual tracking of validity and devices often leads to missed updates or revocations. MDM tools automate the process, removing manual intervention.
3 Key Metrics for Automation
Metric 1: Automated Issuance
When a new device joins the enterprise, can the tool automatically generate the appropriate certificate, eliminating the hassle of manually selecting the certificate type and filling in parameters? This evaluation criteria includes two aspects:
- Certificate templates: Can the "Device Group - Certificate Template" association be pre-set (e.g., a "Sales Group" template is bound to a Wi-Fi certificate, and a "R&D Group" template is bound to a VPN certificate) so that the template is automatically applied when a new device joins the group?
- Automatic format conversion: Android devices commonly use PEM and DER formats, while enterprises may obtain certificates from CAs in PFX format. Verify that the tool can automatically convert these formats.
Metric 2: Automated Renewal
Certificate expiration is the most common risk factor, and the tool's automated renewal directly determines whether business interruptions can be avoided. Key considerations during the evaluation include:
- Multi-dimensional alerts: In addition to backend notifications, is email support supported (covering all IT team communication scenarios)?
- Automatic, seamless updates: Whether updates require a device reboot or employee cooperation?
- Phased update testing: For core devices (such as hospital monitors and bank POS terminals), compatibility testing of the new certificate is required before batch updates are implemented to mitigate risk.
Metric 3: Automated Revocation
If certificates are not revoked promptly when a device is decommissioned, lost, or an employee leaves, they could be used for unauthorized access. During the assessment, focus on:
- One-click revocation efficiency: Can certificates be revoked for a single device or group of devices with a single click?
- Emergency freeze functionality: Can certificates be frozen in real time after a device is lost (faster than revocation and suitable for emergency situations)?
- Revocation log completeness: Does it record the reason for revocation, who performed the revocation, and when? This ensures compliance with HIPAA and PCI DSS audit requirements.
Core Feature 3: Policy-Driven Adaptation
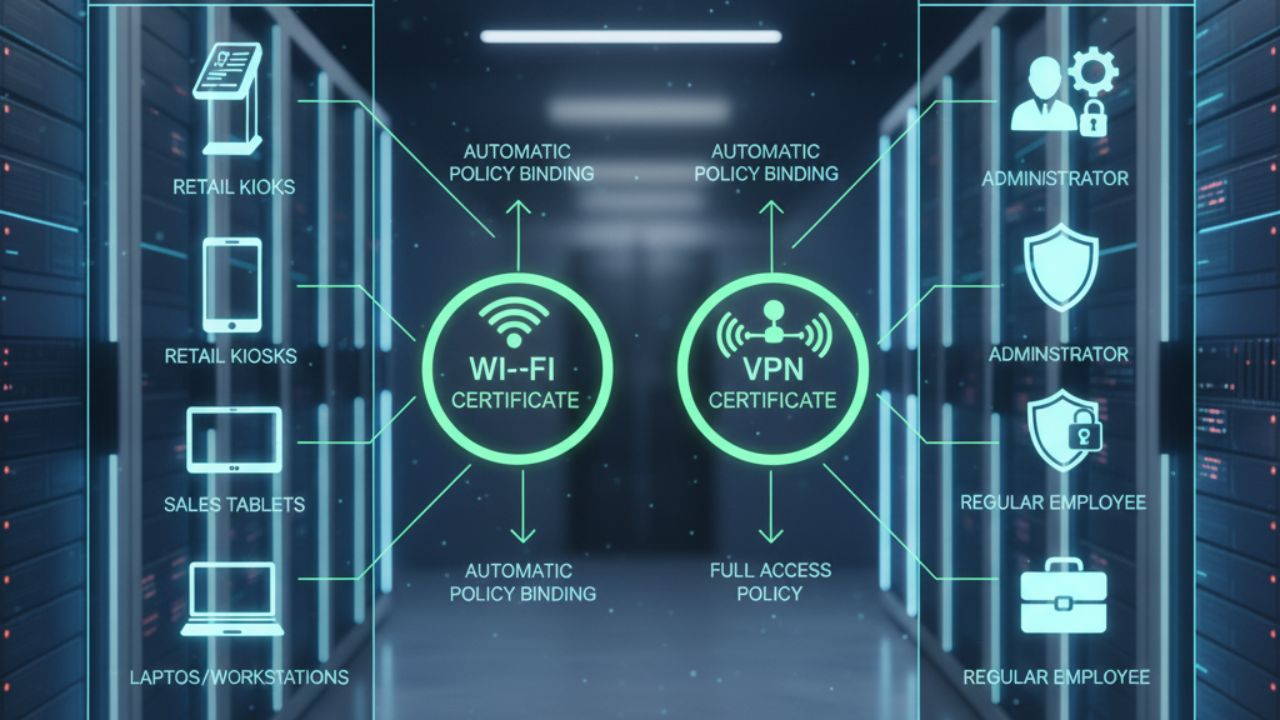
Automated Certificate Policies
Enterprise devices are grouped by department (e.g., “store kiosk group” in retail, “sales tablet group” in enterprises). Each group needs different certificates (Wi-Fi for kiosks, VPN for sales). Employees also have roles (regular staff, administrators) with different certificate needs. Manual management often causes mismatches, like VPN certificates on kiosks or admin certificates for regular staff. Policy-driven MDM tools automatically bind groups and roles to certificates, preventing errors.
2 Key Metrics for Policy Flexibility
Metric 1: Group Policy Adaptation
The evaluation focuses on whether the tool can dynamically respond to changes in device groups. There are two specific criteria:
- Group-certificate binding stability: After creating a device group, is the certificate policy permanently associated? New devices joining the group automatically obtain certificates. AirDroid Business supports two-way group-certificate binding. When devices are added or removed from the group, certificates are automatically synchronized (new devices install certificates, and removed devices delete certificates).
- Cross-group migration adaptability: When a device is moved from group A to group B, does the tool automatically uninstall group A certificates and install group B certificates without manual intervention?
Metric 2: Role-Based Adaptation
In addition to device groups, user roles also affect certificate permissions (e.g., administrators can download certificates, while regular employees can only use them). When evaluating, focus on:
- Role-Permission Association: Can certificate operation permissions be assigned by role?
- Integration with Other MDM Features: Can certificate policies be integrated with features like Kiosk Mode and App Management? For example, AirDroid Business supports "Automatically apply Wi-Fi certificate policies when Kiosk Mode is enabled," ensuring that Kiosk devices can only connect to specific networks and cannot switch networks.
Core Feature 4: Monitoring and Alerts
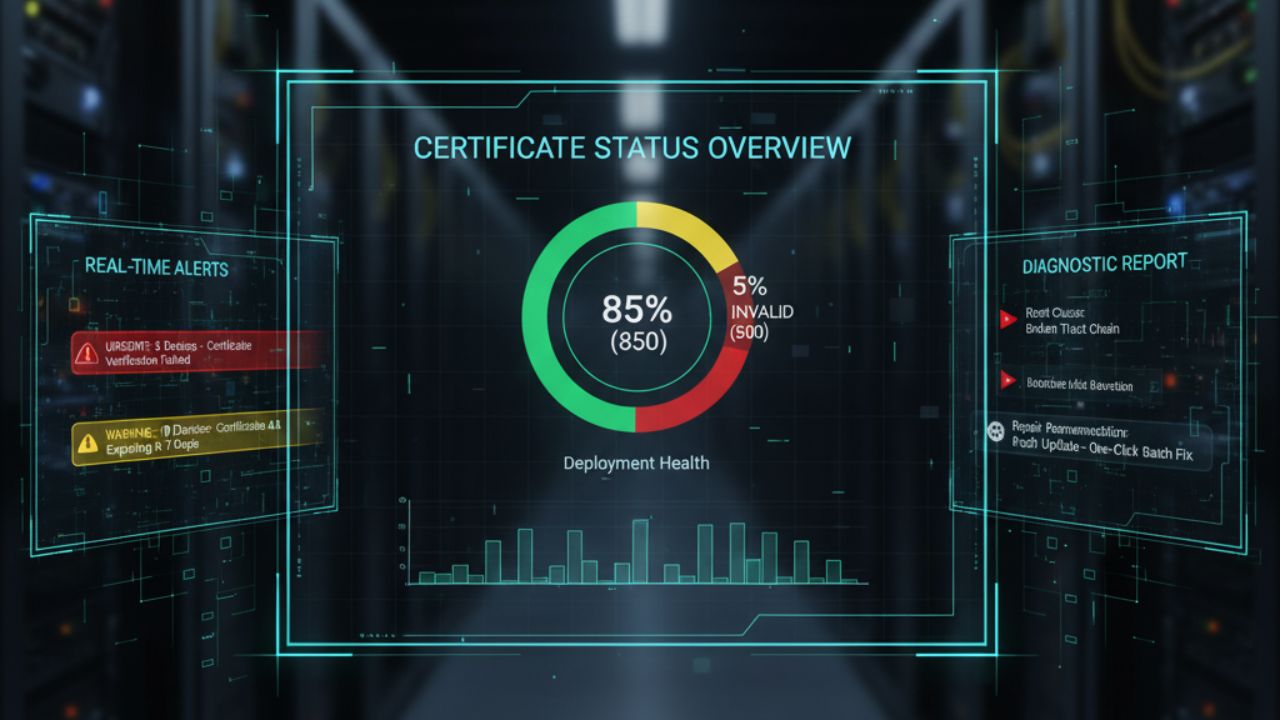
Real-Time Certificate Monitoring
When manually managing certificates, each device must be checked to see if it has a certificate installed, whether the certificate has expired, or whether verification has failed. By the time problems are discovered, business interruptions have often occurred. However, the "status monitoring + alarm" feature of MDM tools allows problems to be "exposed early and located quickly."
3 Key Metrics for Monitoring
Metric 1: Real-Time Status
The first thing to consider during the evaluation is whether the tool can intuitively display the status of all certificates. Specific criteria include:
- Visual Dashboard: Does it have a summary interface that displays the total number of certificates, valid certificates, expired certificates, and invalid certificates, as well as the percentage of each status, for a clear overview?
- Detailed Query: Can you search by device ID/group name/certificate type to view the validity period, deployment time, and verification history of individual device certificates? Support for viewing the certificate's historical operation log (e.g., who deployed and updated the certificate) for easy traceability?
- Abnormal Status Flagging: Does it automatically flag abnormal devices such as those with verification failures, format errors, or broken trust chains?
Metric 2: Alert Triggers
During the evaluation, it's important to confirm whether the tool covers all key exception scenarios, focusing on:
- Completeness of alert types: Does it support alerts such as "certificate expiration, verification failure, deployment failure, and leak risk"?
- Diversity of alert methods: In addition to backend pop-ups, does it support simultaneous alerts via email and SMS to ensure IT staff don't miss any of them?
- Customizable alert thresholds: Can you set trigger conditions, such as "alert if deployment fails on more than 5 devices" or "alert if expired certificates exceed 10 devices"?
Metric 3: Diagnostics
Troubleshooting certificate issues is a major pain point for IT personnel, and the tool's ability to provide diagnostic assistance directly impacts troubleshooting efficiency. During the evaluation, focus on:
- Built-in diagnostic tools: Whether they can automatically detect the cause of the issue.
- Clear repair recommendations: Whether the report provides detailed repair steps.
- Batch repair support: If multiple devices fail due to the same cause (e.g., a broken trust chain), can a single-click repair be performed?
Core Feature 5: Seamless Security Integration

Integrating with Existing Systems
Many enterprises already have mature IT systems (such as Active Directory for identity management and self-built PKI systems for certificate issuance). If MDM tools can’t integrate with these systems, “data silos” occur. For example, new PKI certificates must be entered manually into the MDM system, and operation logs manually imported into the audit system. An MDM tool with secure integration enables data sharing and unified permissions, embedding certificate management into existing systems.
3 Key Metrics for Integration
Metric 1: PKI Integration
The evaluation focuses on whether the tool supports mainstream PKI protocols and systems. Specific criteria include:
- Completeness of protocol support: Does it support mainstream protocols such as LDAP, SAML 2.0, OAuth 2.0, and PKCS#12? AirDroid Business supports all common PKI protocols and can integrate with mainstream systems such as Microsoft AD CS and WoSign PKI.
- Real-time data synchronization: Does the MDM system synchronize new and revoked certificates in real time?
- Unified permissions management: Can PKI/AD accounts be used to log in to the MDM system, achieving single sign-on (SSO)?
Metric 2: IT System Integration
In addition to PKI, MDM also needs to integrate with systems such as OA, audit, and CRM. When evaluating, focus on:
- API accessibility: Whether open API interfaces are provided to support custom integration.
- Log export compatibility: Whether logs can be exported in CSV/PDF format, and whether fields meet audit system requirements (e.g., including "operator, device ID, time, and certificate ID"); Third-party application integration: Whether integration with commonly used enterprise tools is supported.
Metric 3: Compliance
During the integration process, the transmission and storage security of certificate data is crucial. The assessment also includes confirming:
- Transmission encryption: Is data encrypted using TLS 1.3 during integration? All AirDroid Business integration interfaces use TLS 1.3 encryption to prevent data interception during transmission.
- Storage encryption: Is the synchronized certificate data stored using AES-256 encryption after integration?
- Compliance certification: Does the MDM tool have security certifications such as ISO 27001 and SOC 2? Can the integration meet compliance requirements such as HIPAA, PCI DSS, and GDPR?
Core Feature 6: Multi-Scenario Linkage

Coordinating Certificates and Business Functions
Standalone certificate management only addresses the "identity and encryption" issue.
If separated from MDM functions like kiosk mode and app management, it can create security vulnerabilities. For example, a kiosk may restrict features but still connect to illegal Wi-Fi, risking data leaks. Multi-scenario certificate linkage embeds certificate security into business processes, delivering dual protection: “functionality restrictions + certificate control.”
3 Key Metrics for Linkage
Metric 1: Kiosk Mode Linkage
Kiosk devices (such as retail kiosks and exhibition kiosks) are a core use case for certificate linkage. Key assessments include:
- Wi-Fi/Network Linkage: When enabled in Kiosk mode, can the device automatically bind to a specific Wi-Fi certificate, preventing the device from connecting to networks without a certificate?
- Offline Certificate Protection: Can certificate validity be verified even when the Kiosk device is offline, preventing security issues from becoming invalid after the device is offline?
Metric 2: App Management Linkage
Linking certificate and app management can eliminate the problem of "installing risky apps in kiosk mode." During the assessment, focus on:
- App signing certificate verification: Is only apps with enterprise code signing certificates allowed to be installed? Unsigned or third-party apps are automatically blocked.
- App update certificate verification: When an app is updated, is the signing certificate re-verified to prevent tampering with the update package?
Metric 3: Multi-Scenario Linkage
Complex business scenarios require a combination of "Kiosk + Application + Network" linkage. During the assessment, confirm the following:
- Customizable combination policies: Can a combination policy of "Kiosk mode + Wi-Fi certificate + App signing certificate" be created and applied to a device group with one click?
- Linkage log tracing: Is there a log record of the linkage between certificates and business functions (such as binding a certificate when opening a kiosk) for compliance auditing purposes?
Link Business Functions with AirDroid Business
Enhance security with multi-scenario certificate linkage. AirDroid Business provides comprehensive protection for your operations.
Three Pitfalls to Avoid in MDM Tool Evaluation
Pitfall 1: Practical Application
Many MDM tools advertise "supporting over 100 features," but the actual operation is complex, and IT staff may not be able to use them even after a week of learning. These “feature-stacked” tools raise management costs. Evaluation should use real-world operation: IT staff must verify core functions like “batch deployment, policy settings, and certificate linkage”. If tasks take over five steps or 30 minutes, the tool isn’t user-friendly.
Pitfall 2: After-Sales Support
Certificate management issues often require urgent action (e.g., device disconnection, certificate leakage, or invalid linkage). Slow support responses from tool vendors can lead to prolonged business interruptions. When evaluating, proactively inquire about support details:
- Support availability: Is support provided 24/7, or only on weekdays (e.g., 9:00 AM to 6:00 PM)?
- Response speed: What is the promised first response time?
- Support methods: Is remote assistance available?
Pitfall 3: Scalability
The number of devices in an enterprise will increase as business expands (e.g., opening new stores, hiring new employees). If a tool's scalability is poor, it can lead to lags and functional failures when the device count exceeds the limit, requiring costly tool replacements. During the evaluation, it's important to confirm scalability details:
- Maximum supported device count: Does the vendor provide a clear "maximum supported device count"?
- Performance test reports: Does it provide performance test data for 1,000+/5,000+ devices (e.g., deployment time, linkage policy activation speed, system utilization rate)?
- Upgrade costs: Does the increase in device count require additional upgrade fees?
Choosing the Right MDM Tool
To transform the above analysis into a practical and actionable tool, the following provides a layered approach to evaluating suppliers.
Six Core Features + Three Pitfalls
The core logic of this evaluation checklist is to compare vendors based on the enterprise's actual pain points (rather than simply the presence of features):
- Small and medium-sized enterprises (50-500 devices): Prioritize "centralized deployment, lifecycle management, and certificate linkage" to address the core pain points of "low efficiency, missed updates, and disconnected functionality."
- Medium and large enterprises (500+ devices): Focus on "policy-driven, security integration, and multi-scenario linkage" to address the management needs of "multiple device groups, complex systems, and diverse business scenarios."
- All enterprises must avoid the pitfalls of "unimplemented features, poor support, and poor scalability" to avoid purchasing products that are unusable.
Evaluation Dimension | Description | Alternatives When Missing | Applicable Enterprise Types |
|---|---|---|---|
| Core Function Evaluation | Certificate Lifecycle Management (including expiration warning) | ● ≤100 devices: Excel + shared calendar ● 100-500 devices: Office software bots ● ≥500 devices: Lightweight plugins | All enterprises, with focus on healthcare/finance |
| Centralized Bulk Deployment Capability | ● ≤50 devices: Manual per-device ● ≥50 devices: Recommend tool replacement | Enterprises with ≥50 devices | |
| Multi-scenario Certificate Linking (Kiosk/Application) | ● ≤30 devices: Manual configuration ● ≥30 devices: Choose tools with linkage support | Retail/exhibitions (many kiosks), healthcare | |
| Status Monitoring & Fault Diagnosis | ● ≤50 devices: Manual weekly checks ● ≥50 devices: Recommend tool replacement | Enterprises requiring fault response | |
| Security Integration Capability | No alternatives (recommend tool replacement) | Medium to large enterprises (mature IT architecture) | |
| Pitfall Avoidance Verification | Verification of Core Function Authenticity | If missing in basic version: estimate upgrade costs | All enterprises, especially SMEs |
| After-sales Support Capability | No alternatives (recommend tool replacement) | Healthcare/finance (high loss risk from downtime) | |
| Scalability | For fast-growing enterprises: switch early to unlimited expansion tools | Chain retail and other fast-growing enterprises | |
| Alternative Solution Adaptability | Excel + Calendar Reminder Adaptability | Only suitable for ≤100 devices and enterprises accepting manual maintenance | Small enterprises (budget-limited) |
| Third-party Plugin Adaptability | Suitable for 100-500 devices and enterprises unable to switch tools yet | Medium enterprises (transition stage) |
Evaluation Matrix Usage Instructions
- 1. Scoring: Fully compliant (2 points), partially compliant (1 point), non-compliant (0 points). ≥80% = recommended; 60%–80% = cautious (add substitutes); 60% = not recommended.
- 2. Priority: Check core functions first (alerts / bulk deployment), then pitfalls, finally scalability.
- 3. Alternative positioning: Excel/plugins serve as transitional solutions; long-term recommendation is to switch to tools with native core function support.
From Evaluation to Trial
Just looking at the checklist isn't enough; you need to "test the waters" with a trial. We recommend a three-step approach:
- 1. Create a requirements list: Based on this article, outline your company's core requirements (e.g., "need to support zero-touch deployment of 500 kiosk devices + Wi-Fi certificate linkage + Active Directory integration") and prioritize them.
- 2. Apply for a targeted trial: Contact your MDM vendor (e.g., AirDroid Business), explain your core requirements, and request a trial account with only core features (focusing on testing certificate linkage and batch deployment to avoid distractions from irrelevant features).
- 3. Score your checklist: During the trial, record "batch deployment time, linkage policy activation speed, alert response speed, and integration success rate," then score against the evaluation criteria in this article before considering a purchase.
Choosing the right MDM certificate management tool not only saves IT manpower but also builds a secure "certificate + business" closed loop, safeguarding the company's security and compliance bottom line. We hope this list can help you avoid detours and choose the right tool.
Enhance Your MDM Strategy with AirDroid Business
Ready to optimize your certificate management? AirDroid Business provides a comprehensive MDM solution to secure your enterprise.







Leave a Reply.